QUOTE(Anime4000 @ Jul 30 2024, 02:34 PM)
This very comprehensive report.
I have asked my friend about Route issue, and I have verify with my another friend who use TIME and indeed route is correct.
I also send this report to MCMC along with IPv6 /60 NPTv6/NAT66 issue
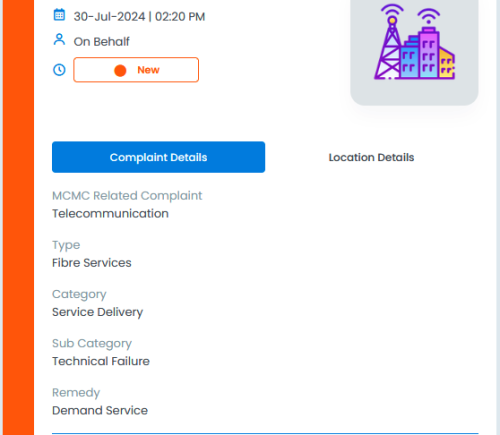
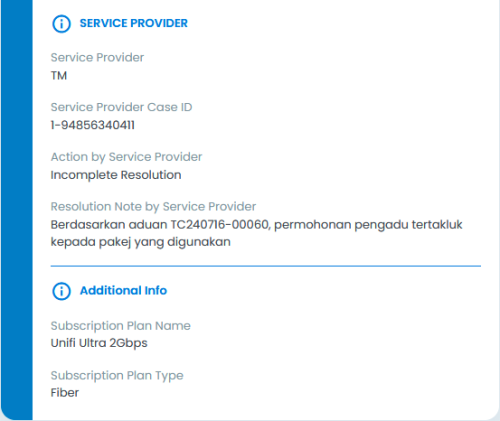
hell, just now MCMC called me, my report sub category going to change to "Service Delivery". So proper team will investigate that TM did not fulfill RFC 6177 and blocking NPTv6/NAT66
Update
kwss Do you think there is hope to have proper IPv6? MCMC just updated and I mention about ISP can get free IPv6 subnet
From a strict technical perspective TM didn't block NPTv6 "directly". What they are doing is not assigning IPv6 address to endpoint and they are just doing prefix delegation with /64.
I believe your focus should be RIPE-690 but since you already mentioned RFC 6177 then just add RIPE-690 to the list. Once correctly implemented, you don't need NPTv6 anymore.
One thing with network operator is nobody likes RFC. Best Current Operational Practice for Operators do a better job to help network operator understand stuff.
If it is up to me to implement RIPE-690, here is how I am going to do it:
First I will submit a plan to APNIC to request another /32 block of IPv6 prefix.
I will keep all the existing setup intact. This is so that people who don't need more address don't need to do anything but still have working IPv6. All the existing router don't need to change.
I will then allow all account holders to request for a static /56 or /48 from the Unifi portal.
The BNG will then route those prefix accordingly.
There are many advantage to this setup:
1. Dynamic IPv6 prefix is useless. You cannot configure it to your Kubernetes cluster, libvirt network, etc when they keep changing.
2. Everyone will have a working IPv6 network by default without complicated setup, as it is now.
3. TM don't need to redo their address planning
QUOTE(Moogle Stiltzkin @ Jul 30 2024, 07:59 PM)
Putin?
 https://www.forbes.com/sites/zakdoffman/202...e-and-election/
https://www.forbes.com/sites/zakdoffman/202...e-and-election/Wouldn't using a VPN solve this? If before people weren't sure, now is more sure that is what you have to do going onwards

It is very easy for a censor with active probe to spot commercial VPN service and it is implemented in Great Firewall of China.
This is how they do it:
1. DPI categorize the connection as VPN.
2. Signal the probe to do active scanning (just like nmap)
3. If the result comes back as positive then put the IP address into the VPN blocklist.
You can easily do this yourself using nmap. All commercial VPN provider has multiple open port to accept different VPN protocol, along with certificate that positively identify themselves.
Another way for censor to identify VPN is they have inside access to social network. If they don't like your post, they will "subpoena" your information and just add the IP address and the active probe signature to VPN blocklist. This will effectively cut off your VPN access because your IP is blocked outright.
Borrowing the principle from Tor, many China citizen workaround this by connecting to CDN which act as a guard node, which then connects to their compute instance acting as exit node.
ACL will be deployed in exit node to block attempt of active probe. AWS has made doing this very easy with their managed prefix list:
https://aws.amazon.com/blogs/networking-and...zon-cloudfront/By using EC2 Instance Endpoint Connect you do not need to expose your SSH port too. So your exit node will have absolutely zero open port for the censor's probe to scan:
https://docs.aws.amazon.com/AWSEC2/latest/U...using-eice.htmlBy doing this, even if the censor blacklist your exit node IP address, your VPN still works because you are not connecting directly to it.
I have a working anti-censorship VPN and have done extensive threat modelling and pen testing on it. I even tested it in China.
Of course the active probe can also detect if your CDN is acting as a front door to bypass censorship and there are various ways to bypass it.
This is a more advanced topic for the censor and I should disclose nothing to educate them. Let's see if the Malaysia censor is as competent as China.


 Jul 30 2024, 11:04 PM
Jul 30 2024, 11:04 PM

 Quote
Quote

 0.0345sec
0.0345sec
 0.56
0.56
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled