QUOTE(surrodox2001 @ Aug 11 2024, 08:36 PM)
Computer security 101: Don't leave default settings unchecked before going with the settings, it may leave nasty security holes behind...
What you said is very true but in practice it is difficult.
I want to use this as case study:
South Korean telecom company attacks customers with malware — over 600,000 torrent users report missing files, strange folders, and disabled PCs
https://www.tomshardware.com/tech-industry/...nd-disabled-pcsGiven the staggering number of PC they infected without triggering Windows Defender or other security software, you can be sure this is some custom shit. A telco can do this, let that sink in for a while.
Until you wireshark your network, you won't realize how hard is it to prevent leakages. I believe it is not apparent to many people their beloved software from Apple and Mozilla came with DNS kill-switch. Common wisdom says the network must do the work to block it, not just toggle a kill-switch.
NTPMajority are unencrypted and cannot be switched to NTS. Example being all router / IoT.
SNIUnfixable until major CDN and DNS provider do something about ECH. It requires a HTTPS DNS records as well as CDN support. Right now Cloudflare has it permanently disabled with no ETA when it will be enabled. Amazon never bother. Akamai? What is that?
Just by looking at the SNI, people can derive what software I am using, when I last updated my software, what I am doing at what time, etc. In fact this is the method FBI and Europol uses to indict people in court.
DNSJust look at all the mess when software libraries with their own DNS lookup logic. With everyone moving to DoH / DoT on their router, how many of them actually perform proper certificate validation? Since ECH requires the HTTPS DNS record, anyone not using secure DNS can have that record removed by attacker and your ECH is effectively dead.
Did I mention how Apple makes it difficult to mess with DNS? It has the most anti-user DNS configuration on earth.
Captive portalAll of them use plaintext HTTP probe. The problem is they contains the full User-Agent. Anyone snooping on the network will know what OS, version and browser you are using. As far as I can tell, all OS and browser performs captive check. Mercenary spyware make use of this to decide which payload to be deployed.
All the above is what came out of my mind right now. I am sure there are more. By the way we are just talking about network security and haven't touch on software and the privacy part of it.
Many Linux distro are also stubborn in using plaintext HTTP for update. Their argument is: We perform GPG checking on the package before install.
Not only does the attacker knows what distro you are using, they also know the exact binary you are installing. So much for OpSec...
This post has been edited by kwss: Aug 12 2024, 01:00 AM 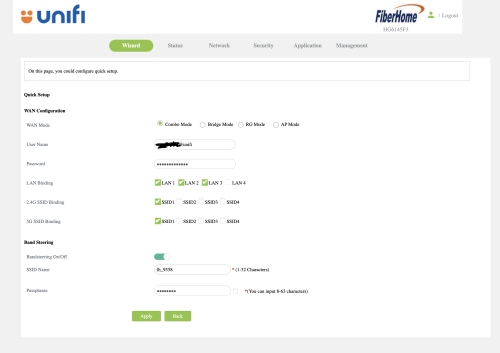


 Aug 11 2024, 02:27 PM
Aug 11 2024, 02:27 PM

 Quote
Quote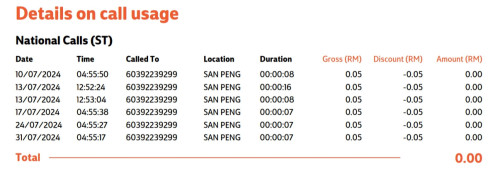
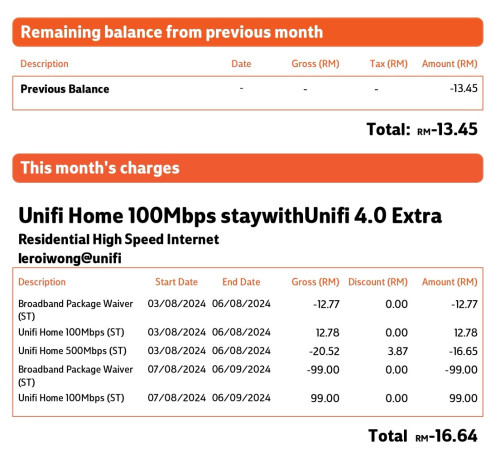
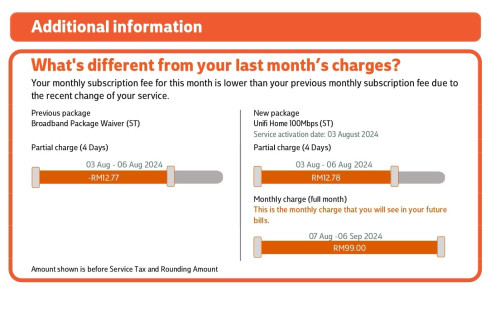
 0.0247sec
0.0247sec
 0.26
0.26
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled