Well I did the password change but also end up having unauth transaction on my card. If not for the SMS then it would have gone unnoticed.
Chat CIMB kena hack?
Chat CIMB kena hack?
|
|
 Dec 20 2018, 09:18 PM Dec 20 2018, 09:18 PM
|
 
Junior Member
149 posts Joined: Jun 2009 |
Well I did the password change but also end up having unauth transaction on my card. If not for the SMS then it would have gone unnoticed.
|
|
|
|
|
|
 Dec 20 2018, 09:18 PM Dec 20 2018, 09:18 PM
Show posts by this member only | IPv6 | Post
#1642
|
     
Senior Member
1,793 posts Joined: Jun 2010 |
|
|
|
 Dec 20 2018, 09:24 PM Dec 20 2018, 09:24 PM
Show posts by this member only | IPv6 | Post
#1643
|
      
Senior Member
3,669 posts Joined: Apr 2006 |
|
|
|
 Dec 20 2018, 09:30 PM Dec 20 2018, 09:30 PM
Show posts by this member only | IPv6 | Post
#1644
|
     
Senior Member
1,793 posts Joined: Jun 2010 |
QUOTE(JohnLai @ Dec 20 2018, 09:24 PM) They don't want admit and cause too much troubles to everyone. You can see in cimb fb. More cases are happening and all complaints from angry customers. I think cimb even turn off pages rating. I cant rate. |
|
|
 Dec 20 2018, 09:35 PM Dec 20 2018, 09:35 PM
Show posts by this member only | IPv6 | Post
#1645
|
   
Junior Member
553 posts Joined: Mar 2018 |
QUOTE(heinlein @ Dec 20 2018, 04:14 PM) https://www.facebook.com/113376605363982/po...999957/?app=fbl This kind of case is old. Not just cimb but alot of other banks where the owner not carefull enuf to take care of their card.You scroll down and find kc chan's comment 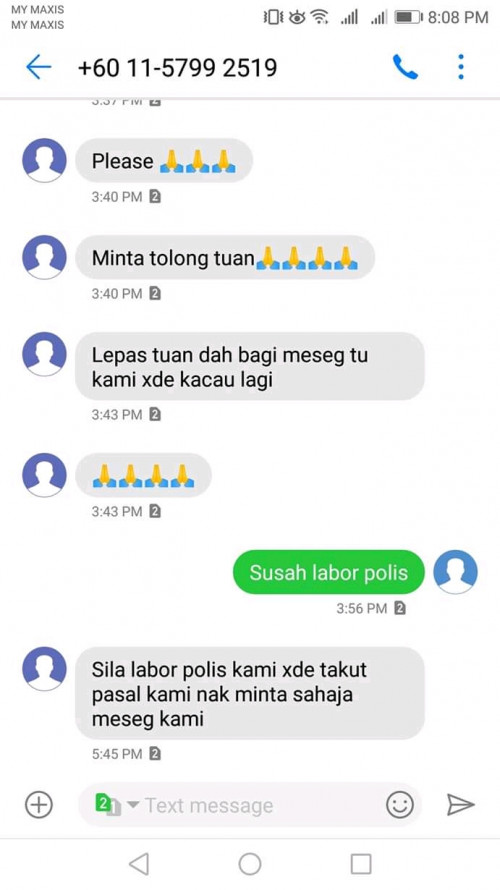 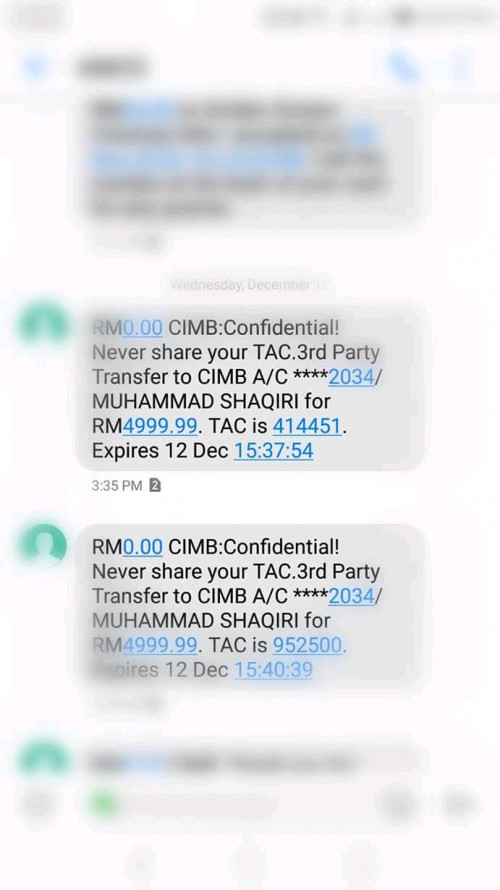 |
|
|
 Dec 20 2018, 09:37 PM Dec 20 2018, 09:37 PM
Show posts by this member only | IPv6 | Post
#1646
|
     
Senior Member
1,793 posts Joined: Jun 2010 |
|
|
|
|
|
|
 Dec 20 2018, 09:54 PM Dec 20 2018, 09:54 PM
Show posts by this member only | IPv6 | Post
#1647
|
   
Junior Member
553 posts Joined: Mar 2018 |
|
|
|
 Dec 20 2018, 10:00 PM Dec 20 2018, 10:00 PM
|
 
Junior Member
149 posts Joined: Jun 2009 |
@Rhetoric
Obviously only CIMB cards are having this issue currently. So many years and none of my cards have had unauthorized transaction, and my lazada card is never used outside, only on lazada and also very rarely. |
|
|
 Dec 21 2018, 01:38 AM Dec 21 2018, 01:38 AM
|
     
Senior Member
1,021 posts Joined: Mar 2010 |
QUOTE(aminpro @ Dec 19 2018, 04:06 PM) » Click to show Spoiler - click again to hide... « NLT has amended the two articles in question and added a note in the first paragraph for clarity. https://nasilemaktech.com/cimb-did-nothing-...al-explanation/ https://nasilemaktech.com/debunking-mainstr...never-happened/ So in both articles, you imply that old passwords cannot be longer than 8 chars? That means less than 8 chars also can? That's pretty extreme ler ... no minimum length ka? And confirm nobody ever could create passwords > than 8 chars in the past? In the first article you said "old passwords do not support or contain special characters" Then in your 2nd article you said "old password consists of letters, numbers and symbols(just not a requirement)" Got or not? TIA |
|
|
 Dec 21 2018, 01:56 AM Dec 21 2018, 01:56 AM
Show posts by this member only | IPv6 | Post
#1650
|
 
Junior Member
172 posts Joined: Mar 2010 |
But ppl still using CIMB anyway
|
|
|
 Dec 21 2018, 02:26 AM Dec 21 2018, 02:26 AM
Show posts by this member only | IPv6 | Post
#1651
|
     
Senior Member
1,793 posts Joined: Jun 2010 |
QUOTE(okuribito @ Dec 21 2018, 01:38 AM) Adoi, we have the author himself here nobody care about nlt, his article clickbait cuz no trafficSo in both articles, you imply that old passwords cannot be longer than 8 chars? That means less than 8 chars also can? That's pretty extreme ler ... no minimum length ka? And confirm nobody ever could create passwords > than 8 chars in the past? In the first article you said "old passwords do not support or contain special characters" Then in your 2nd article you said "old password consists of letters, numbers and symbols(just not a requirement)" Got or not? TIA |
|
|
 Dec 21 2018, 06:08 AM Dec 21 2018, 06:08 AM
|
 
Junior Member
191 posts Joined: Aug 2010 From: Town of Eureka |
QUOTE(okuribito @ Dec 21 2018, 01:38 AM) Adoi, we have the author himself here The current updated FAQ from CIMB suggests that special characters were allowed in the past, just not mandatory. So in both articles, you imply that old passwords cannot be longer than 8 chars? That means less than 8 chars also can? That's pretty extreme ler ... no minimum length ka? And confirm nobody ever could create passwords > than 8 chars in the past? In the first article you said "old passwords do not support or contain special characters" Then in your 2nd article you said "old password consists of letters, numbers and symbols(just not a requirement)" Got or not? TIA The JS implementation also allows for special characters to be submitted if it was less than 8 characters. The first article was taking the assumptions of how the old system used to work. The second article reflects a more accurate situation due to the currently given evidence. So far we cannot find good evidence that special characters were not allowed during the 8 character era. Everything else points to it being allowed back then. Regarding the 8 characters thing you mentioned earlier, in the past, the characters were fixed to 8 characters maximum and minimum. There was never > 8 characters in the past because it does not exist due to the old password policy being fixed at 8 characters. The JS logic representing the old policy is the one that is saying "less than 8" as a criterion.  All that said, the conclusion is that security was never compromised or hacked due to the new mechanisms for CIMB Clicks as some articles are suggesting in their clickbait headlines This post has been edited by aminpro: Dec 21 2018, 06:19 AM |
|
|
 Dec 21 2018, 06:53 AM Dec 21 2018, 06:53 AM
Show posts by this member only | IPv6 | Post
#1653
|
 
Junior Member
177 posts Joined: Jun 2012 |
Hmmm. CIMB seems to be getting worse. I still prefer the old clicks website. Their staff usually won't layan you also.
|
|
|
|
|
|
 Dec 21 2018, 09:39 AM Dec 21 2018, 09:39 AM
|

Junior Member
5 posts Joined: May 2010 |
QUOTE(aminpro @ Dec 21 2018, 06:08 AM) The current updated FAQ from CIMB suggests that special characters were allowed in the past, just not mandatory. I can assure you that their prev password rules do not support any special characters. Before the new rules roll out, my cimb click password is the only one without any special characters.The JS implementation also allows for special characters to be submitted if it was less than 8 characters. The first article was taking the assumptions of how the old system used to work. The second article reflects a more accurate situation due to the currently given evidence. So far we cannot find good evidence that special characters were not allowed during the 8 character era. Everything else points to it being allowed back then. Regarding the 8 characters thing you mentioned earlier, in the past, the characters were fixed to 8 characters maximum and minimum. There was never > 8 characters in the past because it does not exist due to the old password policy being fixed at 8 characters. The JS logic representing the old policy is the one that is saying "less than 8" as a criterion.  All that said, the conclusion is that security was never compromised or hacked due to the new mechanisms for CIMB Clicks as some articles are suggesting in their clickbait headlines |
|
|
 Dec 21 2018, 09:46 AM Dec 21 2018, 09:46 AM
|
      
Senior Member
2,856 posts Joined: Mar 2012 |
QUOTE(Rhetoric @ Dec 20 2018, 09:35 PM) This kind of case is old. Not just cimb but alot of other banks where the owner not carefull enuf to take care of their card. I think it is not related to users carelessness.I think there is some data leak happened inside CIMB or related to the data backups lost last year. My two friends kena with PayPal unauthorised transaction amounting more than RM100. And the worst part, you need to pay to replace your card eventhough it is not your fault. It is not cheap at all. And just want to tell you someone did post on Twitter that some hacker spam message and is looking to find partner to cash out money from CIMB. |
|
|
 Dec 21 2018, 10:05 AM Dec 21 2018, 10:05 AM
Show posts by this member only | IPv6 | Post
#1656
|
 
Junior Member
164 posts Joined: Mar 2007 |
QUOTE(aminpro @ Dec 21 2018, 06:08 AM) The current updated FAQ from CIMB suggests that special characters were allowed in the past, just not mandatory. Putting “cimb did nothing wrong” in the title is extremely misleading. Se7en’s articles were written with public’s interests at heart. Your article seems to ridicule the people’s concern about security, normalizing the 8 characters limit, and the use if recaptchaThe JS implementation also allows for special characters to be submitted if it was less than 8 characters. The first article was taking the assumptions of how the old system used to work. The second article reflects a more accurate situation due to the currently given evidence. So far we cannot find good evidence that special characters were not allowed during the 8 character era. Everything else points to it being allowed back then. Regarding the 8 characters thing you mentioned earlier, in the past, the characters were fixed to 8 characters maximum and minimum. There was never > 8 characters in the past because it does not exist due to the old password policy being fixed at 8 characters. The JS logic representing the old policy is the one that is saying "less than 8" as a criterion.  All that said, the conclusion is that security was never compromised or hacked due to the new mechanisms for CIMB Clicks as some articles are suggesting in their clickbait headlines |
|
|
 Dec 21 2018, 10:14 AM Dec 21 2018, 10:14 AM
|
 
Junior Member
95 posts Joined: Feb 2017 |
the simple scenario is, the people banked in their hard earned money into cimb.
their money started to vanish without them knowing. who's fault ? the people or cimb ? according to nlt, it would be the people's fault. if u were to say it was some hacker who did it, then it would have to be hacker vs cimb which in turn, is just simply cimb at fault. |
|
|
 Dec 21 2018, 11:32 AM Dec 21 2018, 11:32 AM
|
     
Senior Member
1,021 posts Joined: Mar 2010 |
QUOTE(silverhawk @ Dec 19 2018, 03:41 PM) From what I understand, there were 3 steps to this That makes sense! And I did not even think about storing in encrypted form. But then again, encrypted form is only slightly better than AsIs / plaintext, isn't it? The argument for 1way hash is so that even if server/DB is broken into OR backup media is lost/stolen 1. Passwords were allowed to be 8 or more characters 2. Rules changed, passwords allowed MAX 8 characters 3. Rules changed again, passwords allowed 8-20 characters So if you had a password in (1) that was longer than 8 chars, it was truncated. Maybe the passwords were stored encrypted instead of hashed, so was possible to work out the original password and truncate it for (2). » Click to show Spoiler - click again to hide... « At the end of the day, I think it all hangs on whether passwords were allowed to be > 8 characters in the past (your step1) AND if yes, how they dealt with those when they changed to MAX 8char (your step 2) IF passwords were never allowed to be >8 char, then this substring slicing code is plain stupid because anything without special char & > 8 char MUST be invalid & rejected off the bat! IF passwords were allowed to be > 8 chars, AND if not mandatory changed to 8 char, then the substring slicing is indicative of some downright scary approach to password management Anecdotal evidence I found: This thread in 2014 discussed CIMB's 8 char limit. But could it be that this represents your step 2? Maybe before 2014, > 8 char passwords were allowed? PS: See 2010 T&C below sevenegg said he had password > 8 char before boonhan also said he had longer password before PS: 2010 CIMB Clicks T&C - says minimum 8 chars 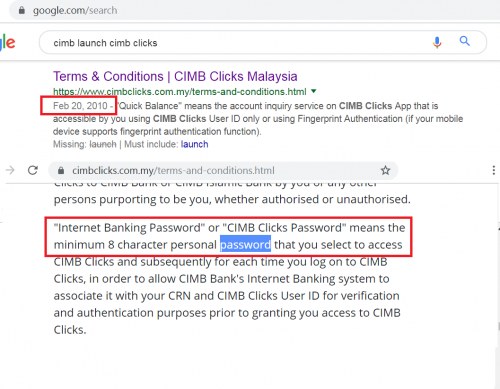 This post has been edited by okuribito: Dec 21 2018, 12:54 PM |
|
|
 Dec 21 2018, 11:35 AM Dec 21 2018, 11:35 AM
|
     
Senior Member
1,453 posts Joined: Dec 2007 |
QUOTE(aminpro @ Dec 21 2018, 06:08 AM) The current updated FAQ from CIMB suggests that special characters were allowed in the past, just not mandatory. lol no. u cant use special characters on cimb password before.The JS implementation also allows for special characters to be submitted if it was less than 8 characters. The first article was taking the assumptions of how the old system used to work. The second article reflects a more accurate situation due to the currently given evidence. So far we cannot find good evidence that special characters were not allowed during the 8 character era. Everything else points to it being allowed back then. Regarding the 8 characters thing you mentioned earlier, in the past, the characters were fixed to 8 characters maximum and minimum. There was never > 8 characters in the past because it does not exist due to the old password policy being fixed at 8 characters. The JS logic representing the old policy is the one that is saying "less than 8" as a criterion.  All that said, the conclusion is that security was never compromised or hacked due to the new mechanisms for CIMB Clicks as some articles are suggesting in their clickbait headlines |
|
|
 Dec 21 2018, 12:12 PM Dec 21 2018, 12:12 PM
Show posts by this member only | IPv6 | Post
#1660
|
   
Junior Member
553 posts Joined: Mar 2018 |
QUOTE(khainiz94 @ Dec 21 2018, 09:46 AM) I think it is not related to users carelessness. Ughh i hate when people just jumped in other people converstation without knowing the issue they are talking about.I think there is some data leak happened inside CIMB or related to the data backups lost last year. My two friends kena with PayPal unauthorised transaction amounting more than RM100. And the worst part, you need to pay to replace your card eventhough it is not your fault. It is not cheap at all. And just want to tell you someone did post on Twitter that some hacker spam message and is looking to find partner to cash out money from CIMB. Paypal abuse you dont have to argue with me, i know its happening. That guy is posting the TAC issue. Paypal dont use TAC. |
| Change to: |  0.0279sec 0.0279sec
 0.53 0.53
 6 queries 6 queries
 GZIP Disabled GZIP Disabled
Time is now: 14th December 2025 - 02:44 AM |