QUOTE(silverhawk @ Dec 19 2018, 03:41 PM)
From what I understand, there were 3 steps to this
1. Passwords were allowed to be 8 or more characters
2. Rules changed, passwords allowed MAX 8 characters
3. Rules changed again, passwords allowed 8-20 characters
So if you had a password in (1) that was longer than 8 chars, it was truncated. Maybe the passwords were stored encrypted instead of hashed, so was possible to work out the original password and truncate it for (2).
» Click to show Spoiler - click again to hide... «
They likely need to slice it because the backend does not know if this is a new/old password format. By right, backend should not care about such things. The fact that they slice says nothing about whether the passwords were stored as hashes or not.
Lets say your very old password was:
"lowyatisthebest"
Then CIMB stupidly changed their rules that passwords must only be 8 characters long, so your password now is:
"lowyatis"
They can hash this value, and since they hash it they will always need the 8 character version of your password to compare with the DB. They don't have to store it as plaintext. Its very unlikely that they are storing passwords in plaintext, wouldn't be able to pass any form of certification/audit if that were the case.
That makes sense! And I did not even think about storing in encrypted form. But then again, encrypted form is only slightly better than AsIs / plaintext, isn't it? The argument for 1way hash is so that even if server/DB is broken into
OR backup media is lost/stolen  as rumored
as rumored, you can still sleep at night. Encrypted means reversible ler. No?
At the end of the day, I think it all hangs on whether passwords were allowed to be > 8 characters in the past (your step1) AND if yes, how they dealt with those when they changed to MAX 8char (your step 2)
IF passwords were never allowed to be >8 char, then this substring slicing code is plain stupid because anything without special char & > 8 char MUST be invalid & rejected off the bat!
IF passwords were allowed to be > 8 chars, AND if not mandatory changed to 8 char, then the substring slicing is indicative of some downright scary approach to password management
Anecdotal evidence I found:
This thread in 2014 discussed CIMB's 8 char limit. But could it be that this represents your step 2? Maybe before 2014, > 8 char passwords were allowed? PS: See 2010 T&C below
sevenegg said he had
password > 8 char beforeboonhan also said he had longer password beforePS:
2010 CIMB Clicks T&C - says minimum 8 chars
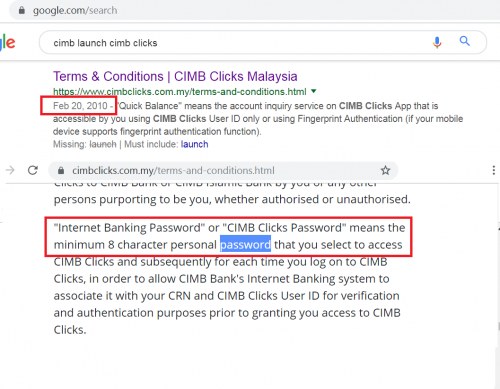 This post has been edited by okuribito: Dec 21 2018, 12:54 PM
This post has been edited by okuribito: Dec 21 2018, 12:54 PM 

 Dec 17 2018, 07:54 PM
Dec 17 2018, 07:54 PM


 Quote
Quote


 0.0632sec
0.0632sec
 0.46
0.46
 7 queries
7 queries
 GZIP Disabled
GZIP Disabled