QUOTE(kwss @ Sep 7 2024, 07:48 AM)
Care to post of output of the command:
CODE
nmap -sCV -Pn -p 53,443,853 dns.google
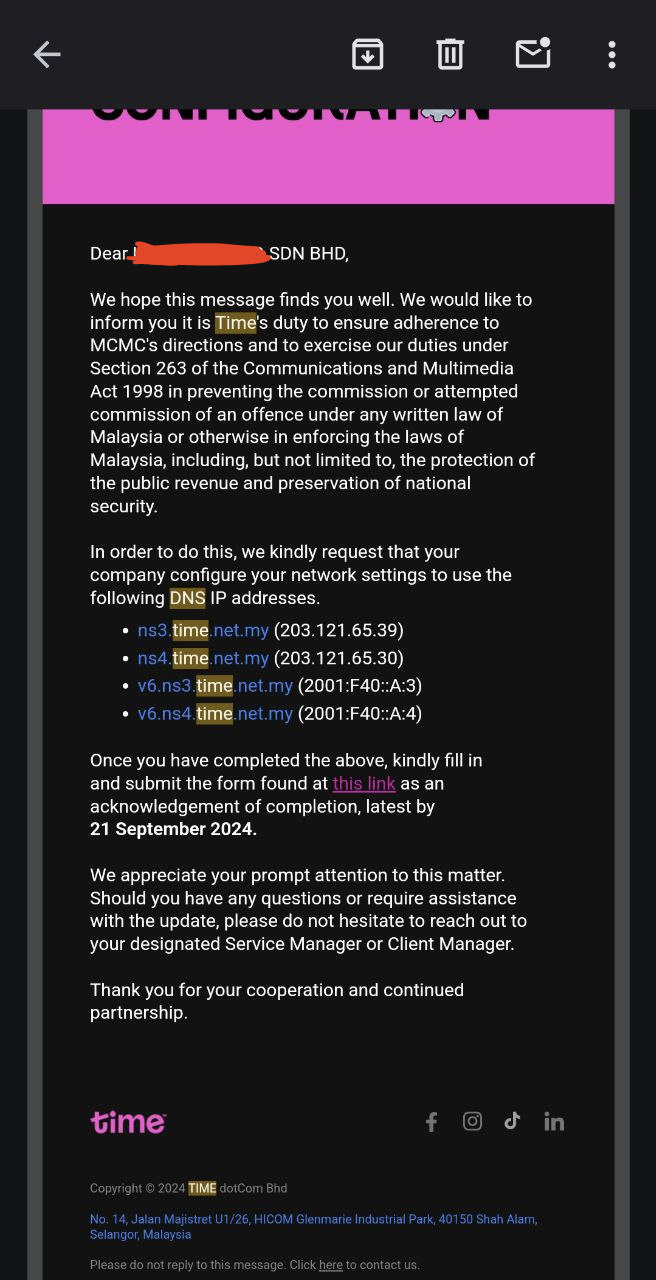
TIME Residential
CODE
nmap scan report for dns.google (8.8.4.4)
Host is up (0.0038s latency).
Other addresses for dns.google (not scanned): 2001:4860:4860::8844
PORT STATE SERVICE VERSION
53/tcp open tcpwrapped
443/tcp open ssl/https HTTP server (unknown)
|_http-title: Google Public DNS
| ssl-cert: Subject: commonName=dns.google
| Subject Alternative Name: DNS:dns.google, DNS:dns.google.com, DNS:*.dns.google.com, DNS:8888.google, DNS:dns64.dns.google, IP Address:8.8.8.8, IP Address:8.8.4.4, IP Address:2001:4860:4860:0:0:0:0:8888, IP Address:2001:4860:4860:0:0:0:0:8844, IP Address:2001:4860:4860:0:0:0:0:6464,
IP Address:2001:4860:4860:0:0:0:0:64
| Not valid before: 2024-08-12T07:19:55
|_Not valid after: 2024-11-04T07:19:54
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 302 Found
| X-Content-Type-Options: nosniff
| Access-Control-Allow-Origin: *
| Location: https://dns.google/nice%20ports%2C/Trinity.txt.bak
| Date: Fri, 06 Sep 2024 23:50:49 GMT
| Content-Type: text/html; charset=UTF-8
| Server: HTTP server (unknown)
| Content-Length: 247
| X-XSS-Protection: 0
| X-Frame-Options: SAMEORIGIN
| Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000
| <HTML><HEAD><meta http-equiv="content-type" content="text/html;charset=utf-8">
| <TITLE>302 Moved</TITLE></HEAD><BODY>
| <H1>302 Moved</H1>
| document has moved
| HREF="https://dns.google/nice%20ports%2C/Trinity.txt.bak">here</A>.
| </BODY></HTML>
| GetRequest:
| HTTP/1.0 302 Found
| X-Content-Type-Options: nosniff
| Access-Control-Allow-Origin: *
| Location: https://dns.google/
| Date: Fri, 06 Sep 2024 23:50:49 GMT
| Content-Type: text/html; charset=UTF-8
| Server: HTTP server (unknown)
| Content-Length: 216
| X-XSS-Protection: 0
| X-Frame-Options: SAMEORIGIN
| Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000
| <HTML><HEAD><meta http-equiv="content-type" content="text/html;charset=utf-8">
| <TITLE>302 Moved</TITLE></HEAD><BODY>
| <H1>302 Moved</H1>
| document has moved
| HREF="https://dns.google/">here</A>.
| </BODY></HTML>
| HTTPOptions:
| HTTP/1.0 302 Found
| X-Content-Type-Options: nosniff
| Location: https://dns.google/
| Date: Fri, 06 Sep 2024 23:50:49 GMT
| Content-Type: text/html; charset=UTF-8
| Server: HTTP server (unknown)
| Content-Length: 216
| X-XSS-Protection: 0
| X-Frame-Options: SAMEORIGIN
| Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000
| <HTML><HEAD><meta http-equiv="content-type" content="text/html;charset=utf-8">
| <TITLE>302 Moved</TITLE></HEAD><BODY>
| <H1>302 Moved</H1>
| document has moved
| HREF="https://dns.google/">here</A>.
|_ </BODY></HTML>
|_ssl-date: TLS randomness does not represent time
| http-server-header:
| HTTP server (unknown)
|_ scaffolding on HTTPServer2
853/tcp open ssl/domain (generic dns response: SERVFAIL)
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
|_dns-nsid: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=dns.google
| Subject Alternative Name: DNS:dns.google, DNS:dns.google.com, DNS:*.dns.google.com, DNS:8888.google, DNS:dns64.dns.google, IP Address:8.8.8.8, IP Address:8.8.4.4, IP Address:2001:4860:4860:0:0:0:0:8888, IP Address:2001:4860:4860:0:0:0:0:8844, IP Address:2001:4860:4860:0:0:0:0:6464,
IP Address:2001:4860:4860:0:0:0:0:64
| Not valid before: 2024-08-12T07:19:55
|_Not valid after: 2024-11-04T07:19:54
2 services unrecognized despite returning data. If you know the service/version, please submit
the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port443-TCP:V=7.94SVN%T=SSL%I=7%D=9/7%Time=66DB9559%P=x86_64-pc-linux-g
SF:nu%r(GetRequest,23A,"HTTP/1\.0\x20302\x20Found\r\nX-Content-Type-Option
SF:s:\x20nosniff\r\nAccess-Control-Allow-Origin:\x20\*\r\nLocation:\x20htt
SF:ps://dns\.google/\r\nDate:\x20Fri,\x2006\x20Sep\x202024\x2023:50:49\x20
SF:GMT\r\nContent-Type:\x20text/html;\x20charset=UTF-8\r\nServer:\x20HTTP\
SF:x20server\x20\(unknown\)\r\nContent-Length:\x20216\r\nX-XSS-Protection:
SF:\x200\r\nX-Frame-Options:\x20SAMEORIGIN\r\nAlt-Svc:\x20h3=\":443\";\x20
SF:ma=2592000,h3-29=\":443\";\x20ma=2592000\r\n\r\n<HTML><HEAD><meta\x20ht
SF:tp-equiv=\"content-type\"\x20content=\"text/html;charset=utf-8\">\n<TIT
SF:LE>302\x20Moved</TITLE></HEAD><BODY>\n<H1>302\x20Moved</H1>\nThe\x20doc
SF:ument\x20has\x20moved\n<A\x20HREF=\"https://dns\.google/\">here</A>\.\r
SF:\n</BODY></HTML>\r\n")%r(HTTPOptions,21A,"HTTP/1\.0\x20302\x20Found\r\n
SF:X-Content-Type-Options:\x20nosniff\r\nLocation:\x20https://dns\.google/
SF:\r\nDate:\x20Fri,\x2006\x20Sep\x202024\x2023:50:49\x20GMT\r\nContent-Ty
SF:pe:\x20text/html;\x20charset=UTF-8\r\nServer:\x20HTTP\x20server\x20\(un
SF:known\)\r\nContent-Length:\x20216\r\nX-XSS-Protection:\x200\r\nX-Frame-
SF:Options:\x20SAMEORIGIN\r\nAlt-Svc:\x20h3=\":443\";\x20ma=2592000,h3-29=
SF:\":443\";\x20ma=2592000\r\n\r\n<HTML><HEAD><meta\x20http-equiv=\"conten
SF:t-type\"\x20content=\"text/html;charset=utf-8\">\n<TITLE>302\x20Moved</
SF:TITLE></HEAD><BODY>\n<H1>302\x20Moved</H1>\nThe\x20document\x20has\x20m
SF:oved\n<A\x20HREF=\"https://dns\.google/\">here</A>\.\r\n</BODY></HTML>\
SF:r\n")%r(FourOhFourRequest,278,"HTTP/1\.0\x20302\x20Found\r\nX-Content-T
SF:ype-Options:\x20nosniff\r\nAccess-Control-Allow-Origin:\x20\*\r\nLocati
SF:on:\x20https://dns\.google/nice%20ports%2C/Trinity\.txt\.bak\r\nDate:\x
SF:20Fri,\x2006\x20Sep\x202024\x2023:50:49\x20GMT\r\nContent-Type:\x20text
SF:/html;\x20charset=UTF-8\r\nServer:\x20HTTP\x20server\x20\(unknown\)\r\n
SF:Content-Length:\x20247\r\nX-XSS-Protection:\x200\r\nX-Frame-Options:\x2
SF:0SAMEORIGIN\r\nAlt-Svc:\x20h3=\":443\";\x20ma=2592000,h3-29=\":443\";\x
SF:20ma=2592000\r\n\r\n<HTML><HEAD><meta\x20http-equiv=\"content-type\"\x2
SF:0content=\"text/html;charset=utf-8\">\n<TITLE>302\x20Moved</TITLE></HEA
SF:D><BODY>\n<H1>302\x20Moved</H1>\nThe\x20document\x20has\x20moved\n<A\x2
SF:0HREF=\"https://dns\.google/nice%20ports%2C/Trinity\.txt\.bak\">here</A
SF:>\.\r\n</BODY></HTML>\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port853-TCP:V=7.94SVN%T=SSL%I=7%D=9/7%Time=66DB955E%P=x86_64-pc-linux-g
SF:nu%r(DNSVersionBindReqTCP,20,"\0\x1e\0\x06\x81\x82\0\x01\0\0\0\0\0\0\x0
SF:7version\x04bind\0\0\x10\0\x03");



 Sep 6 2024, 09:44 PM
Sep 6 2024, 09:44 PM

 Quote
Quote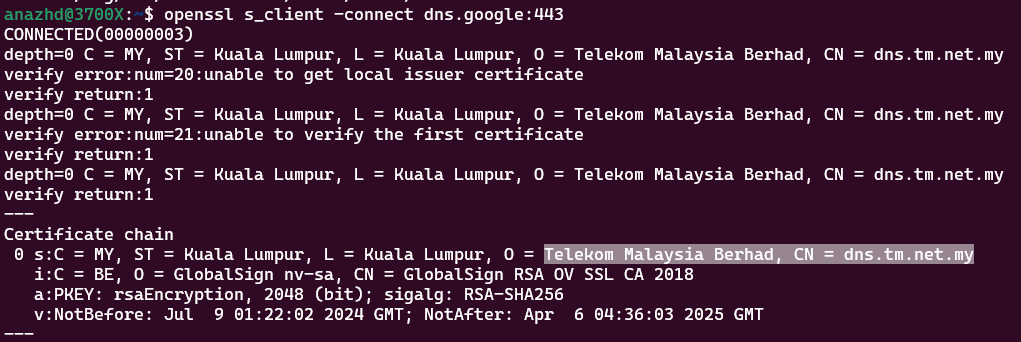
 0.0234sec
0.0234sec
 0.62
0.62
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled