Source 1
Source 2
I guess this is possible if we're only using the cleartext dns of both google dns and cloudflare dns ie
google dns:
CODE
8.8.8.8
8.8.4.4
2001:4860:4860::8888
2001:4860:4860::8844
cloudflare dns:
CODE
1.1.1.1
1.0.0.1
1.1.1.2
1.0.0.2
1.1.1.3
1.0.0.3
2606:4700:4700::1111
2606:4700:4700::1001
2606:4700:4700::1112
2606:4700:4700::1002
2606:4700:4700::1113
2606:4700:4700::1003
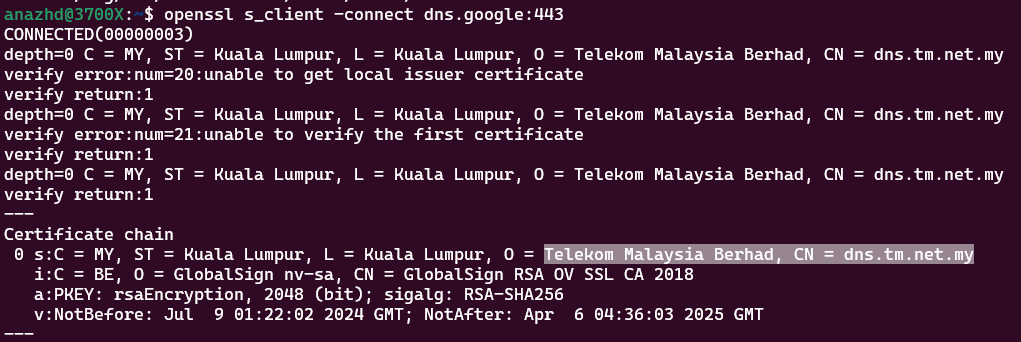
Haven't tested myself but I'm 100% sure the
CODE
8.8.8.8
and CODE
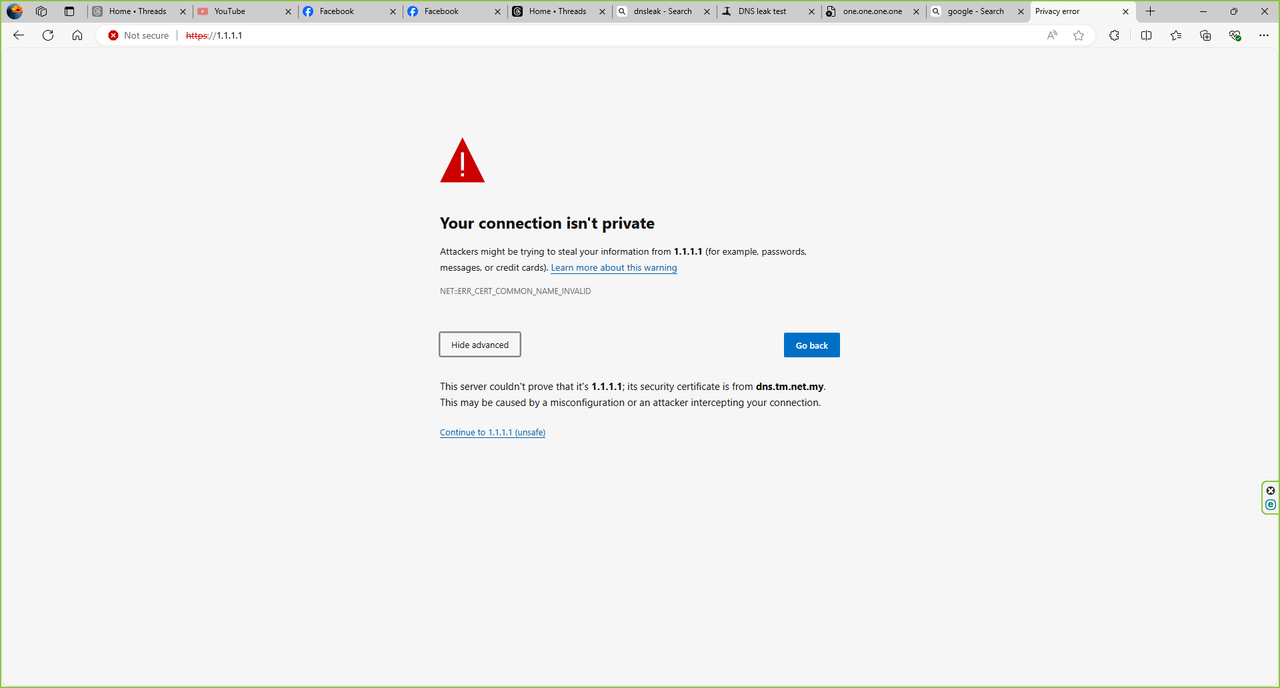
1.1.1.1
are hijacked since both are the popular dns ip for google dns and cloudflare dns. Others on the list might be hijacked too depending on telco network admins.But basically people, its high time we should stop using cleartext dns. Its unsecured and hijackable. Start using encrypted dns everywhere.
Theres plenty of them listed here. You'd want to use either the dns-over-https aka doh or dns-over-tls aka dot.
Modern system already support using those encrypted dns protocol ie android natively via setting. Should be listed as
CODE
Private DNS
in phone setting. You should add a dns-over-tls server here, omit the CODE
tls://
from uri if you copy paste from the list above.Ios and mac is native too via dns profile. If prefer app can use dnsecure.
Linux can natively too if install any local forwarding dns server like bind9 or dnsmasq. If prefer gui, theres technitium dns server and adguardhome.
Windows can use yoga dns server.
Ty for attending my ted talk lmao.
This post has been edited by axxer: Aug 8 2024, 11:53 AM


 Aug 8 2024, 11:35 AM, updated 2y ago
Aug 8 2024, 11:35 AM, updated 2y ago
 Quote
Quote
 0.0206sec
0.0206sec
 0.39
0.39
 7 queries
7 queries
 GZIP Disabled
GZIP Disabled