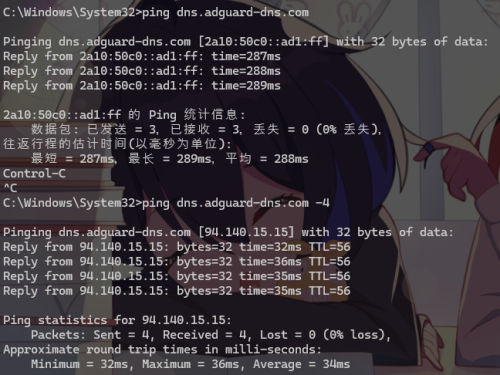
I play a bit with Celcom's implementation. Basically they catch all UDP port 53 on IPv4 and IPv6
Test with fc00:: which is a non-routable local address
CODE
dig @fc00:: pornhub.com
; <<>> DiG 9.18.28 <<>> @fc00:: pornhub.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 29836
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;pornhub.com. IN A
;; ANSWER SECTION:
pornhub.com. 3600 IN A 175.139.142.25
;; Query time: 37 msec
;; SERVER: fc00::#53(fc00::) (UDP)
;; WHEN: Sat Aug 10 02:16:04 +08 2024
;; MSG SIZE rcvd: 56
Test with 10.10.10.10 which is also non-routable:
CODE
dig @10.10.10.10 pornhub.com
; <<>> DiG 9.18.28 <<>> @10.10.10.10 pornhub.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 28827
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;pornhub.com. IN A
;; ANSWER SECTION:
pornhub.com. 3600 IN A 175.139.142.25
;; Query time: 44 msec
;; SERVER: 10.10.10.10#53(10.10.10.10) (UDP)
;; WHEN: Sat Aug 10 02:16:19 +08 2024
;; MSG SIZE rcvd: 56
Using non-routable IPv6 address but with TCP:
CODE
dig @fc00:: pornhub.com +tcp
;; Connection to fc00::#53(fc00::) for pornhub.com failed: host unreachable.
;; no servers could be reached
;; Connection to fc00::#53(fc00::) for pornhub.com failed: host unreachable.
;; no servers could be reached
;; Connection to fc00::#53(fc00::) for pornhub.com failed: host unreachable.
;; no servers could be reached
Using non-routable IPv4 address but with TCP:
CODE
dig @10.10.10.10 pornhub.com +tcp
;; Connection to 10.10.10.10#53(10.10.10.10) for pornhub.com failed: timed out.
;; no servers could be reached
;; Connection to 10.10.10.10#53(10.10.10.10) for pornhub.com failed: timed out.
;; no servers could be reached
;; Connection to 10.10.10.10#53(10.10.10.10) for pornhub.com failed: timed out.
;; no servers could be reached
This means that using TCP should work, even if it is plain text. Yes it does!
CODE
dig @1.1.1.1 pornhub.com +tcp
; <<>> DiG 9.18.28 <<>> @1.1.1.1 pornhub.com +tcp
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48352
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;pornhub.com. IN A
;; ANSWER SECTION:
pornhub.com. 14400 IN A 66.254.114.41
;; Query time: 69 msec
;; SERVER: 1.1.1.1#53(1.1.1.1) (TCP)
;; WHEN: Sat Aug 10 02:20:20 +08 2024
;; MSG SIZE rcvd: 56
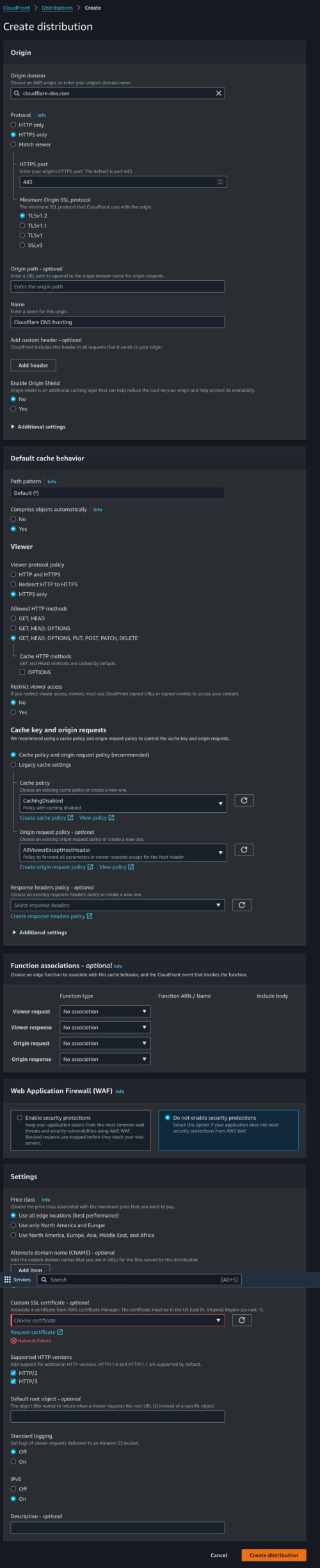
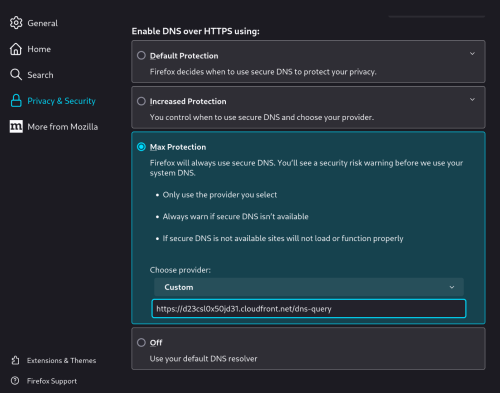
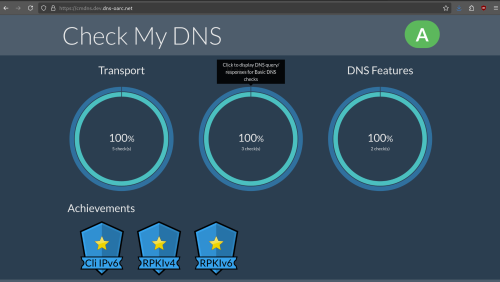
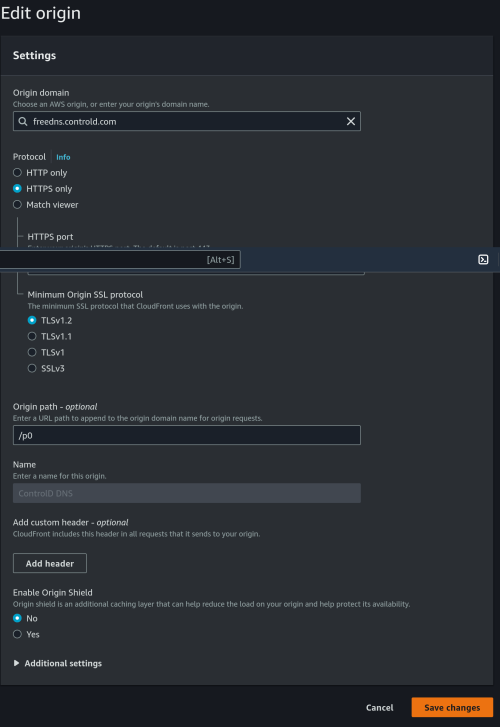
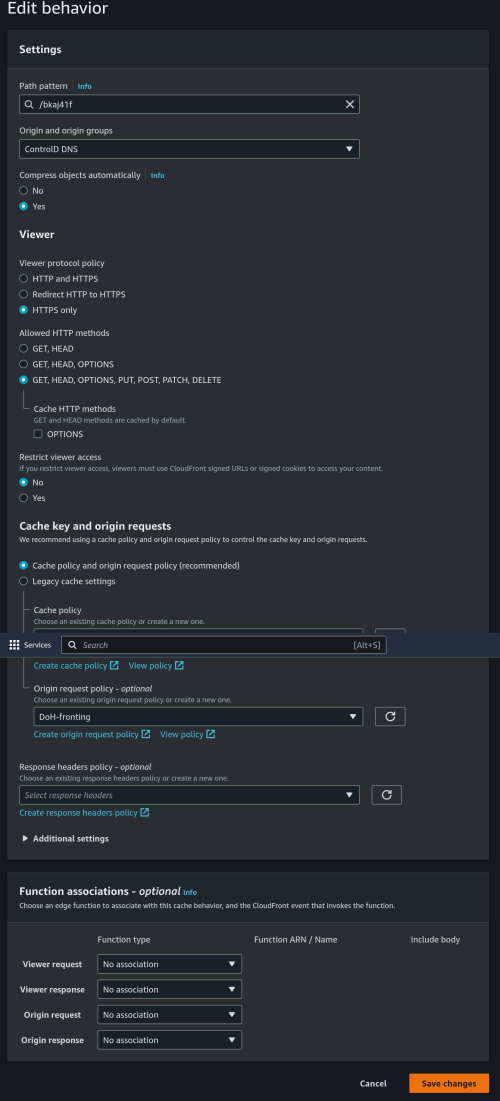
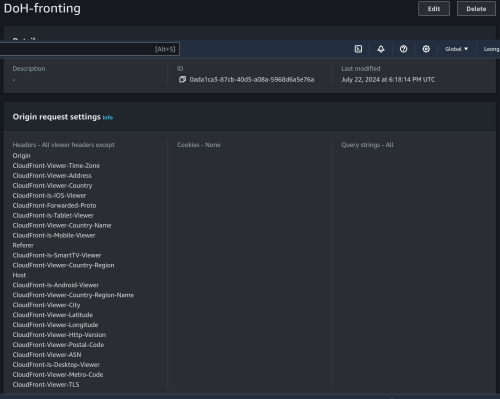
However, I found that they block by IP address too for pornhub.com and xvideos.com. murrayhunter.substack.com didn't have their IP blocked so it is not quite consistent.
Reason is murrayhunter.substack.com uses Cloudflare CDN. They cannot block the CDN without blocking everyone else.
This post has been edited by kwss: Aug 10 2024, 02:44 AM 

 Aug 9 2024, 12:11 AM
Aug 9 2024, 12:11 AM

 Quote
Quote


 0.0216sec
0.0216sec
 0.50
0.50
 7 queries
7 queries
 GZIP Disabled
GZIP Disabled