QUOTE(Hobbez @ Dec 18 2018, 02:34 AM)
Only a few accounts were hacked, but my guess is CIMB is doing damage control when the news break out about how insecure is their accounts. For me, the main problem that I found out is that their passwords only accept the first 8 characters. Which I find out the hard way when I tried to change my password and failed. It keep lying to me and said my ID is invalid (but I could login with that ID).
Let's say your password is 12345678H%&*GGhklp
Anyone can login with your password if they just type in 12345678
If you were stupid enough to put this kind of password, then sorry la....
But CIMB hopes nobody that stupid, so their damage control is to implement that Google Recaptcha to stop brute force password attempts.
And it is easy with bots these days. There are hackers and spammers selling brute force software that they claim can crack most kinds of passwords.
Knowing the length of a password is a big step to cracking it.
Something doesn't seem right to me. Everywhere I look, I'm told that passwords are stored after (one-way) hashing (& even salting), never in its original form.
When you originally set up your password as 12345678H%&*GGhklp, it would have been stored as a certain hash. Any slight diff would result in a totally diff hash. (That's why they say they do not know what your password is)
So what boggles me is how someone can get in when he submits 12345678 - the hash for that would definitely be diff from the hash for 12345678H%&*GGhklp ...No?
The only possibility this can happen is IF at the point you originally set up your password as 12345678H%&*GGhklp, it was truncated to 12345678... damn FUBAR, right? Telling ppl to set up long complex pw & truncating to short



 Dec 18 2018, 11:59 AM
Dec 18 2018, 11:59 AM

 Quote
Quote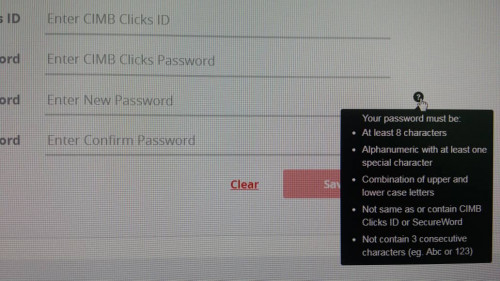
 0.2309sec
0.2309sec
 0.37
0.37
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled