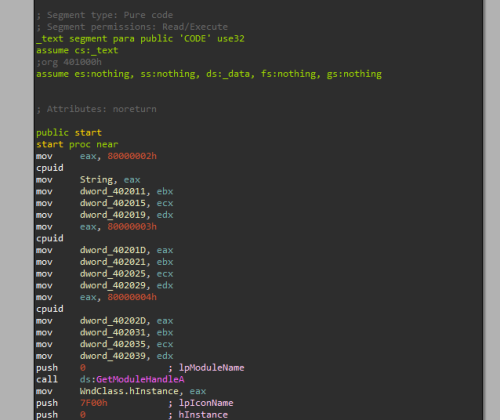
Today I am going to disassemble my own program, called msgbox.exe, written also in fasm.
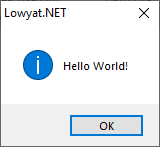
Example msgbox.exe to debug / disassemble
First, download the WinDbg and launch it:
Download debugging tools from Windows SDK
Start menu items of WinDbg after installation
Open WinDbg(x64)
Then, browse to msgbox.exe and open it.
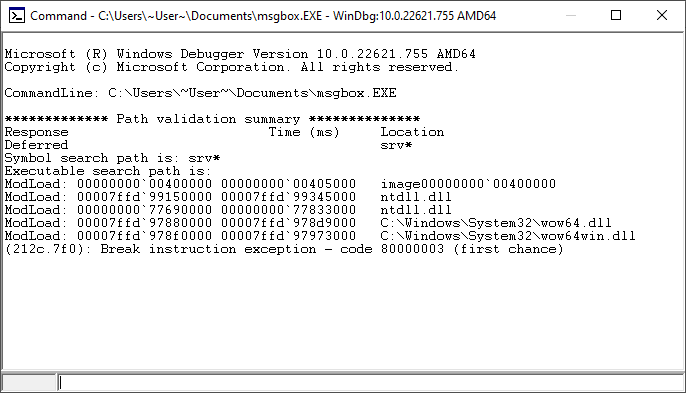
Open executable (msgbox.exe)
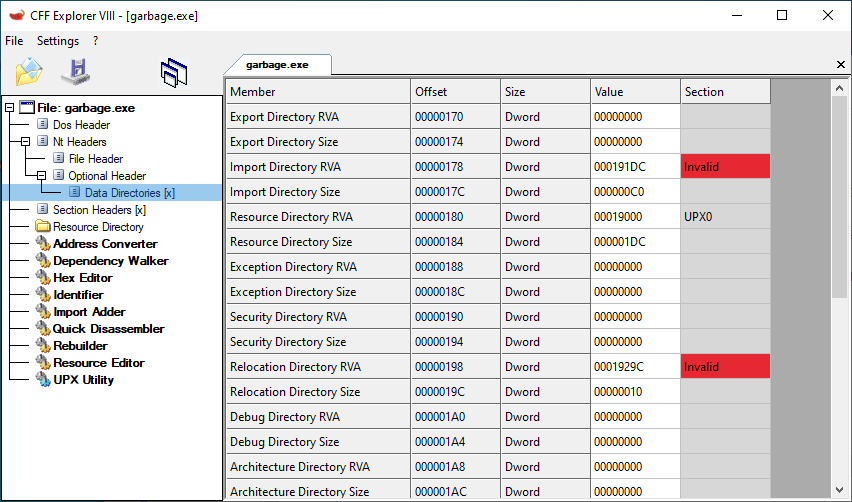
But funny it didn't show a PE header analysis, I have to download a separate PEDump to find which memory to dump.
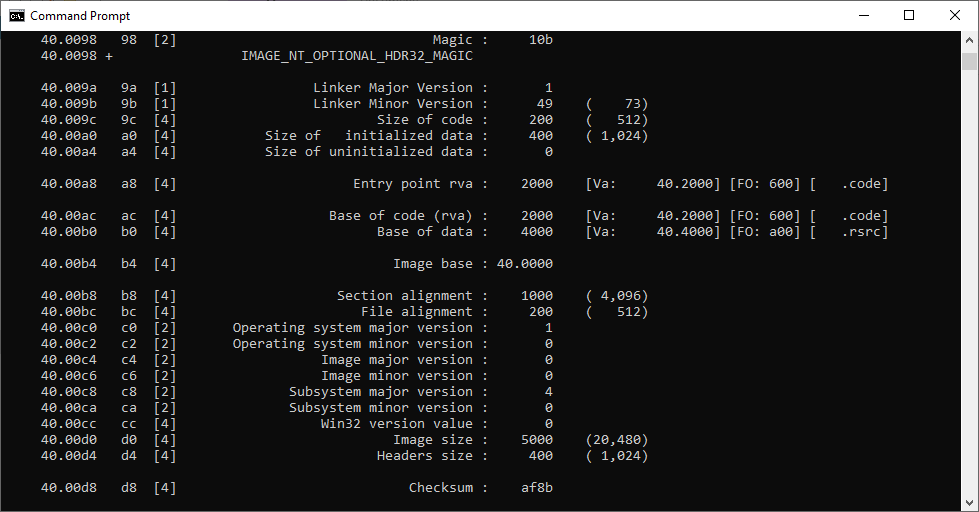
Run PEDump tool to find code section entry point
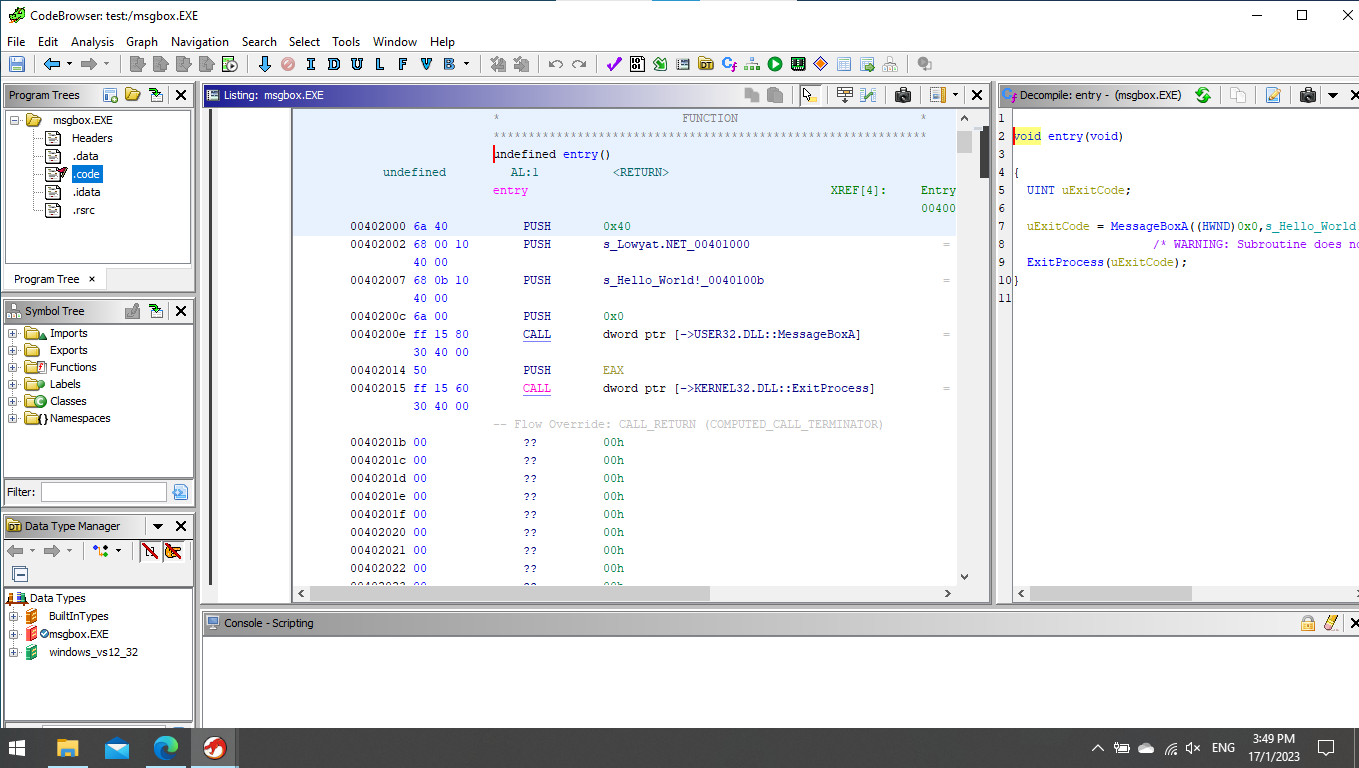
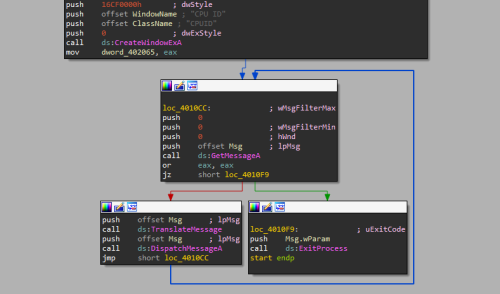
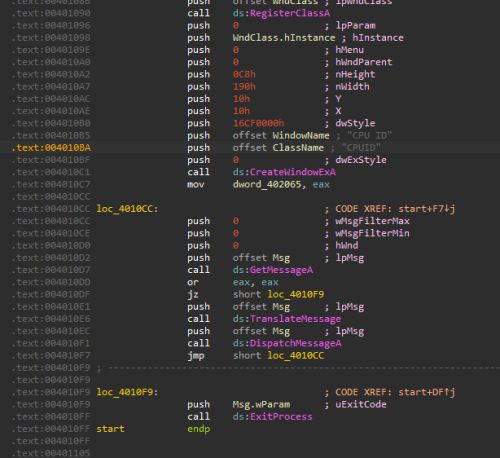
Finally, we got the address: 0x402000, so let's disassemble it.
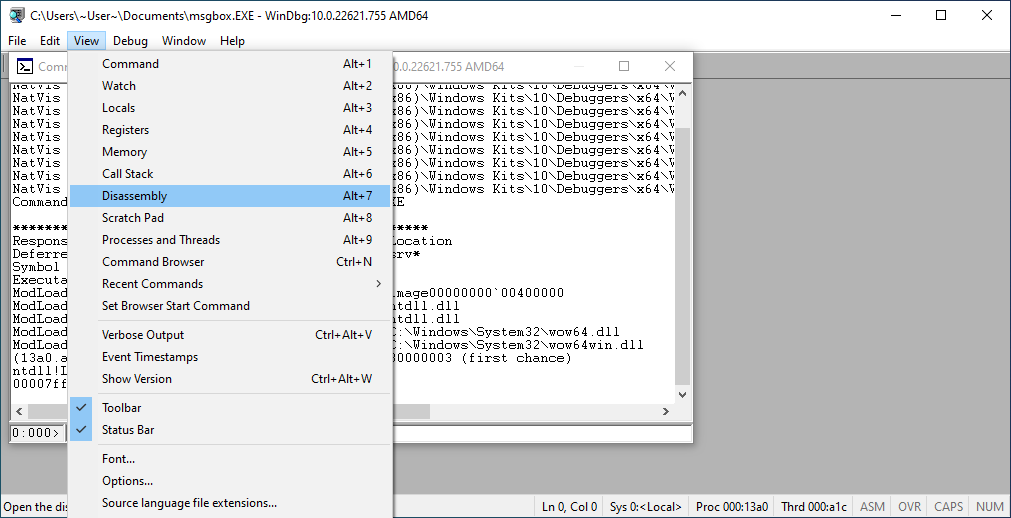
View disassembly
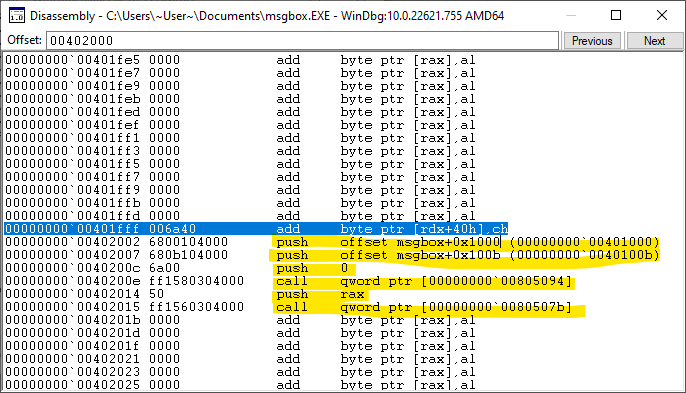
Spot on!
It looks exactly like the source code!
CODE
start:
push 0x40
push title
push message
push 0
call [MessageBox]
push eax
call [ExitProcess]
I know quite a few sifu here, know better in anything disassembly, e.g. junyian, angch and cikelempadey.
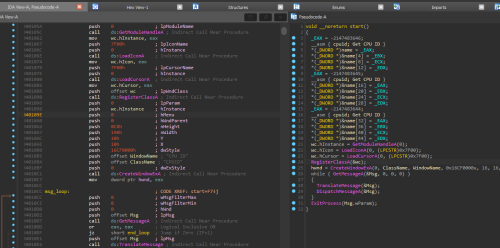
I think I used the wrong tool to disassemble msgbox.exe, because it doesn't bring me directly to the code section of the executable.
Enlightenment please?
PEDump tool: forum.lazarus.freepascal.org/index.php?topic=46617.0
Windows SDK: developer.microsoft.com/en-us/windows/downloads/windows-sdk/


 Jan 17 2023, 01:46 AM, updated 3y ago
Jan 17 2023, 01:46 AM, updated 3y ago
 Quote
Quote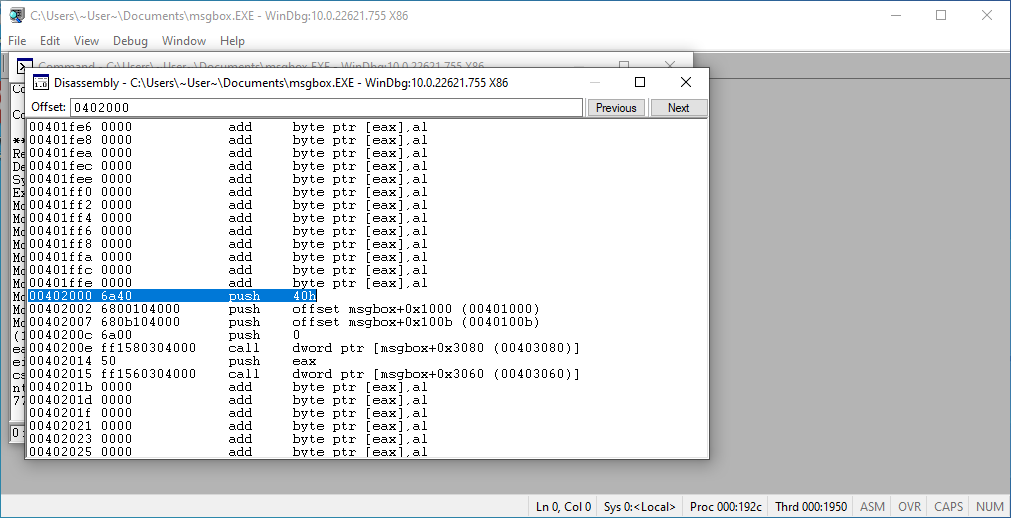

 0.0263sec
0.0263sec
 0.97
0.97
 5 queries
5 queries
 GZIP Disabled
GZIP Disabled