QUOTE(FlierMate4 @ Jan 22 2023, 11:00 PM)
I able to recover portion of the resource section, by editing the raw size value.
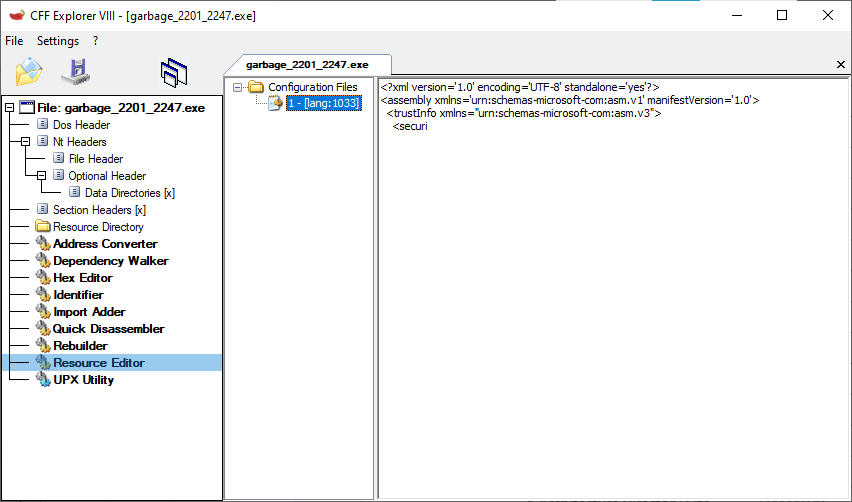
At least now Resource Editor shows some data instead of blank
But UPX Utility still not able to unpack:
CODE
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2011
UPX 3.08w Markus Oberhumer, Laszlo Molnar & John Reiser Dec 12th 2011
File size Ratio Format Name
--------upx: C:\Users\~User~\AppData\Local\Temp\upx1A9E.tmp: OverlayException: invalid overlay size; file is possibly corrupt
------------ ------ ----------- -----------
Unpacked 1 file: 0 ok, 1 error.
Here's what I did, roughly. So I don't spoil your fun

I used CFF Explorer and PE-Bear:-
- CFF Explorer is old and was not updated for many years. But there are some features that I like which I couldn't find in other newer PE editors
- PE-Bear is much newer, and still regularly updated.
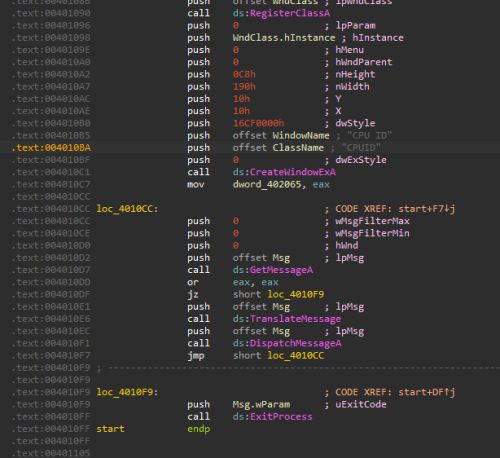
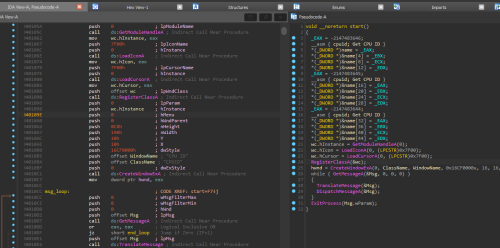
The resource section you found is the first step. But you should know that this incomplete XML is useless, and is not critical for an exe to be recognized as a valid PE file by Windows. So you can safely delete this resource ID. The more important thing is the import directory. As long as this is corrupted or not formed properly, Windows cannot load the exe. When recreating unpacked/decrypted exes/dlls, rebuilding the import table is a common step. You can see that after fixing the .rsrc section, the import table is empty. So you can use CFF Explorer to add your own import table into this.
After that, the exe should be recognized by UPX and you can unpack it nicely. But the exe still can't execute properly again. There's still something wrong with import table, which can be fixed easily by renaming the dll that it's supposed to load. After that we can run the exe and get this.
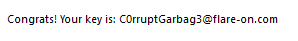


 Jan 17 2023, 10:39 PM
Jan 17 2023, 10:39 PM
 Quote
Quote

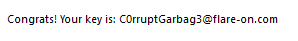
 0.0119sec
0.0119sec
 0.55
0.55
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled