QUOTE(Drewkk @ Sep 13 2018, 02:47 AM)
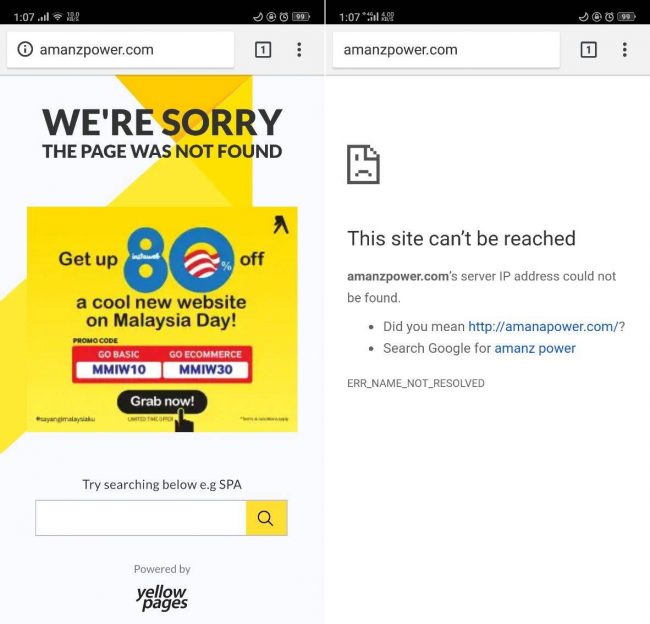
I noticed today that unresolved domains and 404 errors on websites without SSL/TLS are getting hijacked by ads!!!!
https://imgur.com/a/6FDuBgcWTH?
The site behind the ads is
http://www.zygy.com which boasts TM as a customer.
Nothing new... They've been doing this for ages. It's even advertised in yellow pages if I remember correctly. Encountered it back in Streamyx days when using the default DNS server.
Edit: Here it is...
https://www.tm.com.my/nxd/Pages/default.aspxQUOTE(mamakap @ Oct 23 2019, 08:05 AM)
What DNS server are you using? TM default server doesn't seem to support DNSSEC. Google and Cloudflare should work.
QUOTE(SilentVampire @ Sep 13 2018, 02:27 PM)
True, forgot about that

DNSSEC is still the way to go, for ‘secure’ DNS queries.
From my understanding, DNSSEC only protects domains that have DNSSEC properly set up. Even then, it doesn't protect DNS queries from being intercepted. For full protection, DNS over HTTPS or TLS is needed. These are supported by Android 9 and Firefox as well as Google and Cloudflare servers but requires manual set up to enable. In addition, Cloudflare servers do DNSSEC validation by default.
QUOTE(Anime4000 @ Sep 13 2018, 03:09 AM)
on my test, TM do Hijack DNS query.
[attachmentid=10018887]
but... on Windows 10, dont have, maybe DNSSEC ?
it is allowed to Hijack customer traffic ? like replace HTTPS to HTTP ?
Can't reproduce this issue here.
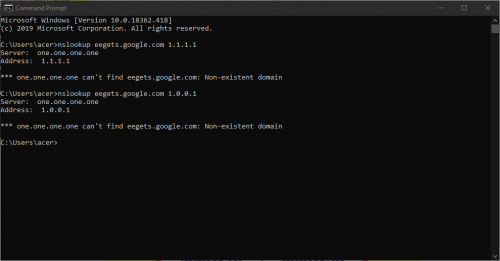
It should be impossible to downgrade HTTPS to HTTP if your browser is working properly and you entered https:// in the URL. It'll just say fail to establish connection.
Edit: Can't reproduce using TM's DNS server too. Maybe they only show ads to some requests or customers?
Edit2: TM doesn't seem to be hijacking DNS requests to Cloudflare for blocked domains:
» Click to show Spoiler - click again to hide... «
CODE
nslookup sayakenahack.com 1.9.1.9
Server: cdns01.tm.net.my
Address: 1.9.1.9
Non-authoritative answer:
Name: sayakenahack.com
Address: 175.139.142.25
nslookup sayakenahack.com 1.1.1.1
Server: one.one.one.one
Address: 1.1.1.1
Non-authoritative answer:
Name: sayakenahack.com
Addresses: 2606:4700:30::6818:6f0b
2606:4700:30::6818:6e0b
104.24.111.11
104.24.110.11


 Sep 15 2018, 12:27 PM
Sep 15 2018, 12:27 PM

 Quote
Quote



 0.0203sec
0.0203sec
 0.26
0.26
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled