QUOTE(Anime4000 @ May 29 2024, 01:27 PM)
I have send mtd14 (ubi_apps) and IoT Module (D-Link Air) to PON Hacking
There is several vulnerabilities:
1. IoT not suppose to run as Root Privilege
2. IoT bind on all Interface (ppp, nas0, nas1, ethX, wlanX) including t-cont
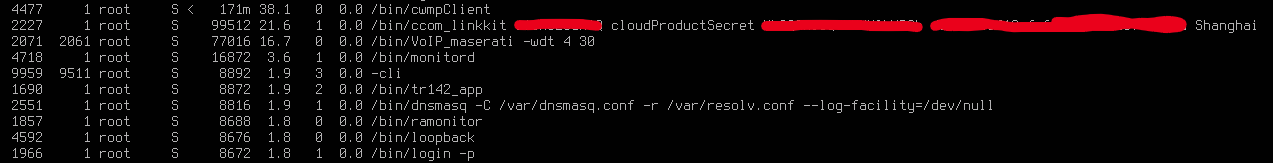
2227 1 root S 99512 21.6 1 0.0 /bin/ccom_linkkit [redacted] cloudProductSecret [redacted] [redacted] Shanghai
1690 1 root S 8872 1.9 2 0.0 /bin/tr142_app
ubi_apps, tr142 and /bin/ccom_linkkit always run as root no matter what, cannot be disable in WebGUI
they found many vulnerability such as common overflow, it can be attack even in Bridge Mode.
I trying to remove from the firmware, it caught on boot loop 😭
It has been suggested that to replace to ability to reply in boot process, this will take time, might more time eradicate any IoT
ubi cannot be disabled because it is used to mount the config partition.There is several vulnerabilities:
1. IoT not suppose to run as Root Privilege
2. IoT bind on all Interface (ppp, nas0, nas1, ethX, wlanX) including t-cont

CODE
2227 1 root S 99512 21.6 1 0.0 /bin/ccom_linkkit [redacted] cloudProductSecret [redacted] [redacted] Shanghai
1690 1 root S 8872 1.9 2 0.0 /bin/tr142_app
ubi_apps, tr142 and /bin/ccom_linkkit always run as root no matter what, cannot be disable in WebGUI
they found many vulnerability such as common overflow, it can be attack even in Bridge Mode.
I trying to remove from the firmware, it caught on boot loop 😭
It has been suggested that to replace to ability to reply in boot process, this will take time, might more time eradicate any IoT
tr142 (kernel module + tr142_app) is loaded via the following path:
insdrv.sh -> rtk_tr142.sh
However I am not sure if it can be easily disabled because it is referenced in the following binary: axel, boa, monitord, omci_app, smuxctl, startup.
You can try nuking it in insdrv.sh and see if the device still boots.
ccom_linkkit is linked inside /bin/startup. Theoretically building a new statically linked ccom_linkkit should work.
CODE
int main()
{
return 0;
}
Depending if they actually check for error code, you might get away with replacing ccom_linkkit with inert binary like id:
CODE
# cp id ccom_linkkit
Also looks like iot-auth-global.aliyuncs.com is actually dead. Depending on which server you hit, you get a 302 to different location. I did not have the hardware to test this, but it seems hardcoded to lookup using the following DNS server: 223.5.5.5, 223.6.6.6, 8.8.8.8.
Completely untested, all based on static analysis and non expert understanding.
This post has been edited by kwss: Jul 24 2024, 09:15 AM


 Jul 24 2024, 09:12 AM
Jul 24 2024, 09:12 AM

 Quote
Quote 0.0169sec
0.0169sec
 0.37
0.37
 7 queries
7 queries
 GZIP Disabled
GZIP Disabled