QUOTE(kwss @ Jul 19 2024, 02:14 AM)
TM is poisoning DNS again. Last time they just outright block port 443, preventing DoH. This time they redirect you to their own server using their own certificate.
$ nmap -sCV -Pn -p 443 1.1.1.1
Starting Nmap 7.93 ( https://nmap.org ) at 2024-07-19 02:09 +08
Nmap scan report for 1.1.1.1
Host is up (0.0093s latency).
PORT STATE SERVICE VERSION
443/tcp open ssl/http EMC Navisphere CIM Object Manager httpd
|_http-title: Site doesn't have a title.
| ssl-cert: Subject: commonName=dns.tm.net.my/organizationName=Telekom Malaysia Berhad/stateOrProvinceName=Kuala Lumpur/countryName=MY
| Subject Alternative Name: DNS:dns.tm.net.my
| Not valid before: 2024-07-09T01:22:02
|_Not valid after: 2025-04-06T04:36:03
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.86 seconds
No wonder yesterday suddenly my android private dns settings suddenly not working.CODE
$ nmap -sCV -Pn -p 443 1.1.1.1
Starting Nmap 7.93 ( https://nmap.org ) at 2024-07-19 02:09 +08
Nmap scan report for 1.1.1.1
Host is up (0.0093s latency).
PORT STATE SERVICE VERSION
443/tcp open ssl/http EMC Navisphere CIM Object Manager httpd
|_http-title: Site doesn't have a title.
| ssl-cert: Subject: commonName=dns.tm.net.my/organizationName=Telekom Malaysia Berhad/stateOrProvinceName=Kuala Lumpur/countryName=MY
| Subject Alternative Name: DNS:dns.tm.net.my
| Not valid before: 2024-07-09T01:22:02
|_Not valid after: 2025-04-06T04:36:03
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.86 seconds
Btw this redirecting will break TLS right? Considering if we use DoH or DoT


 Jul 20 2024, 02:35 AM
Jul 20 2024, 02:35 AM

 Quote
Quote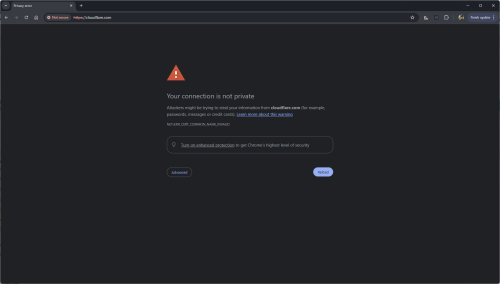
 0.0321sec
0.0321sec
 0.36
0.36
 7 queries
7 queries
 GZIP Disabled
GZIP Disabled