Thanks for sharing me extra IP address, I get different CloudFlare Johor than yours, lol.
Also thanks not sharing the abuse IP address, as it is really abuse. :thumbsup:
I give up, I telling you 99% of times, google DNS give better result, which is Malaysia CDN, and yes, in case it is laggy because MY CDN(Any, Tencent or Akamai or Alibaba) back to SG/HK server caused by crappy TM backbone, then I will switch to one.one.one.one
1. I am not doing that, I just tell everyone, switch to DNS over HTTPS to solve this slowness issues.
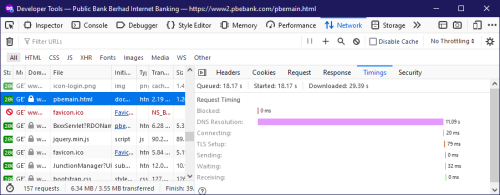
Somehow browser need to obtain DNSKEY from the PBE website server, but DNS over HTTPS might already provide DNSKEY, so there is no 10s delay on opening PBE website for the first time.
5 years ago with that old Chrome it is much worse result, the DNSKEY don't cached and expired during browsing of PBE, I think Firefox and Chrome solved this issues, based on me need to relaunch browser to reproduce this issues.
Also yes, 5 years ago there is no DNS over HTTPS yet.
PS: Might not be the DNSKEY, but I lazy to discover, because the solution is switch to DNS over HTTPS.

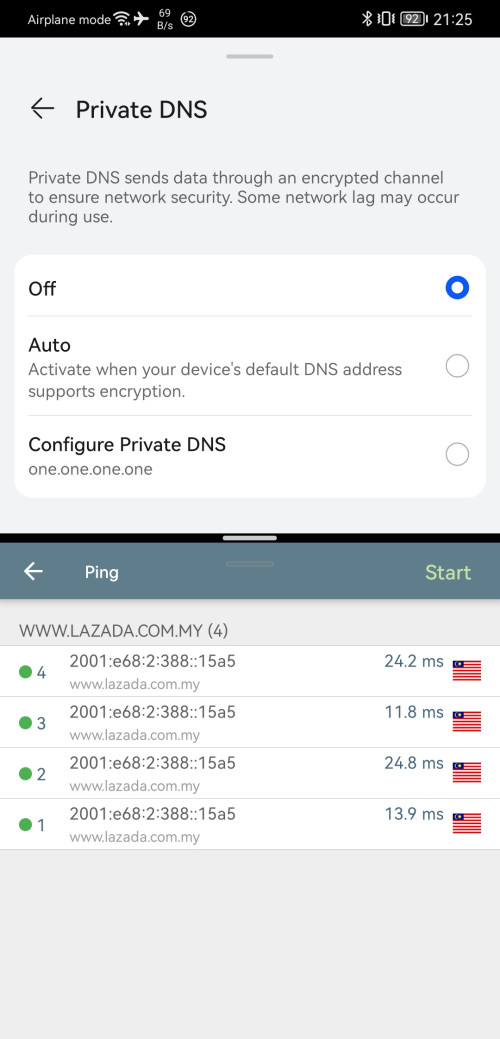
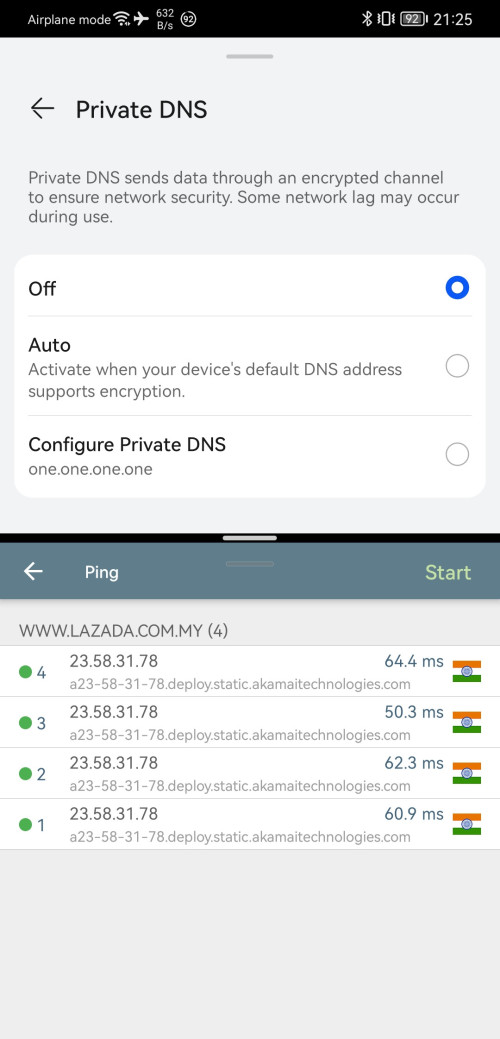
2. I told them to use IPv6 instead of IPv4, all my result pointing to IPv6 provide better routing(cloudflare going to SG for lowyat)and better DNS result because the IPv6 is more precise on where are you(lazada going to MY or SG for any DNS).
I think you have been messed up with someone, I am fine with it lol.
Because I am same line with you, disable IPv6 and thinking it will solve everything?
Hei, how about Steam gamer?
Now Steam all using steamwork that depend on P2P!!!
IPv4 = Steam P2P Relays server
IPv6 = Steam Friend shared IPv6 and directly connected
Also CGNAT.
So, nope, I reject on disabling IPv6, because bad network is better than dead network.
It is just like telling everyone use 5GHz WiFi on IoT, but not thinking it is possible 100 meter passing multiple wall, which 2.4GHz perform better.
How about those get interference at 2.4GHz?
Go 5GHz with router put outdoor, problem solved!
Sadly, most people don't hand-craft like me, written the IP Address into host file as need, not saying Android phone need ROOT or VPN DNS apps to do that, and local VPN burn a lot battery life.
So yes, most of my method don't works well for regular user, which easy to be solved by burn money, going VPN, get new router and IoT supported 5GHz, lol.
Yup, like I said, I share it out, everyone did it, then the traffic to JHB too large, it will still get load-balanced to SG in the end, lol.
And same to the abuse, I think you might have idea about it now.

If, DIG works as real world, how did I get different result from ping???
The screenshot on phone just for simple record, the real world is, I use ping on my computer, the result is same as the screenshot.
I use browser on my PC, result same.
Only DIG is different.
See?
DIG is good, but not when server treat differently to tools and real-world application.
Then you will be like, DIG IS FINE, customer FAULT!!!
So is my fault that DIG get different result from PING that request over DNS UDP, or BEST TRACE, or DNS over HTTPS, or DNS over TLS???
DIG fighting 4 different method to obtain the AAAA and A result, only DIG came out wrong result.
Your conclusion, this guys is fault, DIG is the only ANSWER because it is It is real time. It is reliable. It is battle tested!!!
Your Bowser is doing it wrong, as it get the different result than DIG!!!
Just like Google did to other browser, not chromium based?
Ban this feature!!!
Then you gonna tell all of them, change to Chrome, your own fault using Firefox and Safari!!!
Why use Safari on iOS! go to Chrome!
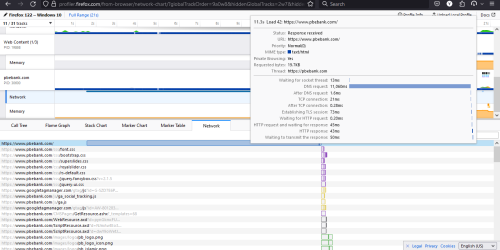
The fault is at DNS side, because same time I run all 4 tools, only DIG get different result, even after ttl, and others 4 changed/updated the result, that's what I observer.
Hmm, thanks for new knowledge, yes, it is trouble for keeping low latency, but not target high bandwidth lol.
So yes, promise is done, 50ms, but crappy because throttling by TM.

Sound funny it is 50ms, but getting throttling to like 1-10 MBPS, and it is enough for CloudFlare, lol.
Fun fact, you know why Google did this?
During the switching on IPv4 to IPv6 few years ago, TM has silently enabled IPv6 support for Streamyx customer, then for the first month, no throttling from Streamyx to Google own server.
Then after they was like DUDE, no more high QoS for normal Streamyx customer!!!
The speed is getting throttling sharp, again(why again? they already throttling to Streamyx user on IPv4), 480 KBPS.
Only method, is just what I did now.
Enforcing Johor CloudFlare server, let the CloudFlare bring the data from SG Server to Johor Server, so I can enjoy my internet.
But I guess you need sharp answer, so here it is.
During that time, IPv6 99% of time it is providing Google server instead of TM peer server, which you can fell the slowdown on Google, 480 KBPS.
Solution?
Hope your IPv4 DNS give you IPv4 result that end up as TM peer server, else, feel the pain of 480 KBPS watching YouTube.(Yes, throttling because YouTube mostly, but it also hurt Google as there are same to TM ISP, lol)
For YouTube that is real pain, because Google choose which very_long_hostname_that_choose_which_IP_you_should_connected.video.youtube.com, so I had to face 3-5 times of wrong result(Google server), then hoping it finally give me TM peer server.
That, forced me to start writing own host files until now, including Bilibili which was using Sina and other server as their free video server hoster during that time, and now, still crappy at HK server back to China Mainland, lol.
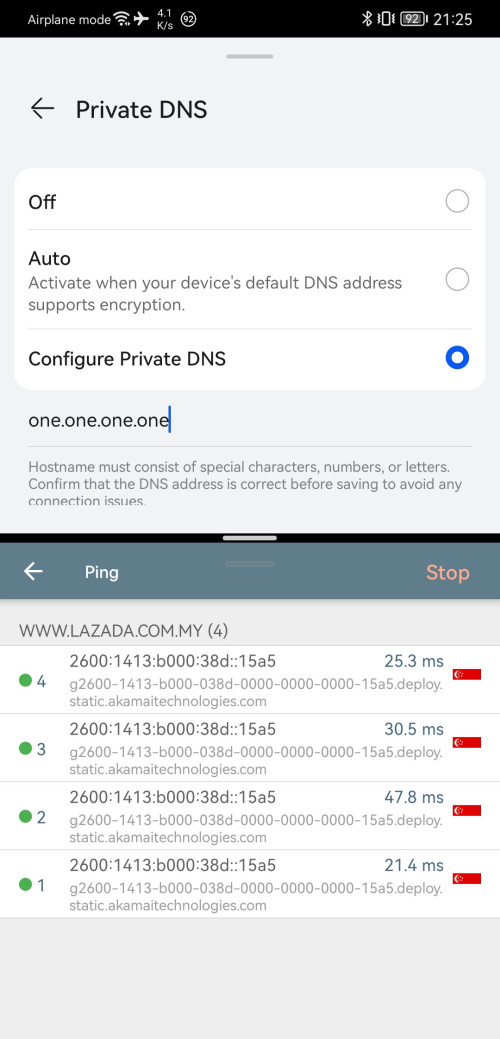
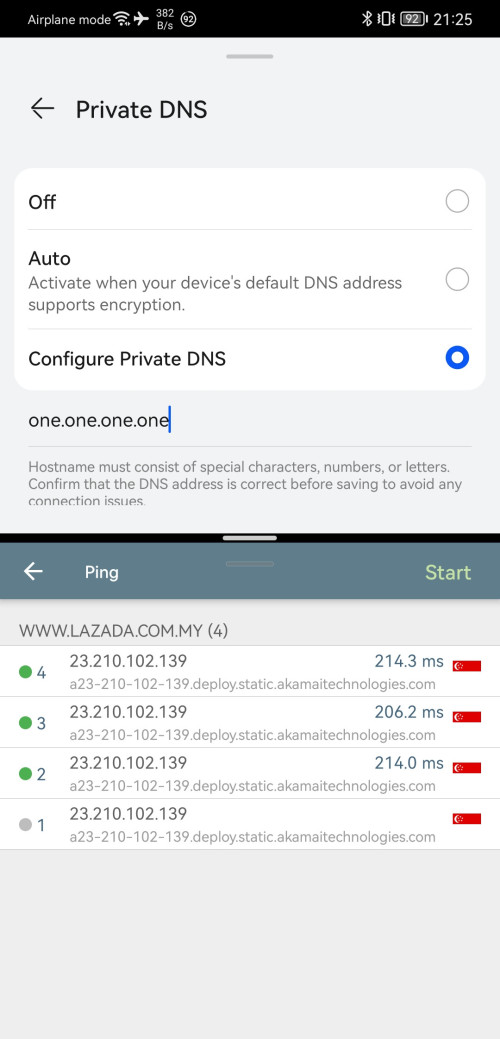
Yes, as above, I will switch as I need, if slowness detected, then jump in between one.one.one.one and google dns la.
Easy.
India is not the problem, because it is still 50ms without random jumping to 200ms and feel the slowness and jitter.
It works fine! As long as no one notify the slowness!
The problem is too heavy throttling on TM side!!!
Wrong, you are not point the error on DNSKEY, which might be the possible, but pointing it is USER PROBLEM again.
You are looking me too down, I am not that stupid, if this is caused by extension, why all website is fine, except PBE?
Remember?
I am firefox user, I know the regular method.
1. Hold shift, safe mode
2. if safe mode fine, then extension error
3. If safe mode failed, then browser or website issues
4. 2=True? Time to perform half-half solution, disable half of your extension, until problem solved, then seek those small range extension.
Anyways, if it end out to be extension, it, will be interesting bug, lol.

----
Tested, nope, not extension, safe mode same issues.

Not a Public Bank customer, fine to me.
Let the Public Bank solve it, not me.
I am other bank's regular customer, lol.

But yes, I might try observe and learn how this happen, so to prevent it happen when I deploy my own la, lol.
Still
Conclusion, based on real world result, not DIG tools.
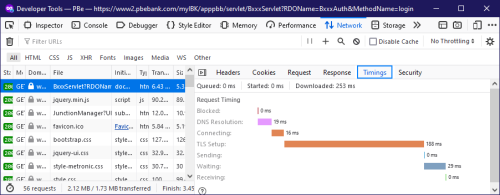
You don't try open Public Bank website on your own side, using Private/Incognito, first-time, uncached, with DNS UDP(not over HTTPS).
You don't try switching one.one.one.one which solved laggy issues during Guess It 2.0 Lazada live event, which solved laggy on livestream video.(by jumping to SG server instead of MY server)
you don't try switching to dot-jp.blahdns.com as private DNS on your Android, which enforce UC Webview engine to happy connect to far server that avoid laggy and deploy(yes, Taobao always forgot to deploy and causing event load failed issues on HK server, lol) issues on Taobao.
(And also using HK DNS server sometimes, or Ali DNS, because Ali DNS IPv4 on Malaysia, but IPv6 on China, lol.)
You, point it out, it is my fault, to doing all those step, to "workaround" TM bad routing issues, workaround Public Bank 10s timeout issues, workaround lazada SG and MY server issues, using host file to using Johor server for CloudFlare issues.
In the end, Yes, it is my fault la, lol.

Now you said it, I am 99% sure your problem will be gone after you delete your host file and reboot.


 Nov 6 2023, 10:24 PM
Nov 6 2023, 10:24 PM
 Quote
Quote


 0.0370sec
0.0370sec
 0.76
0.76
 7 queries
7 queries
 GZIP Disabled
GZIP Disabled