If you miss my previous articles (in forum posts format), here are they:
* First time using WinDbg ( https://forum.lowyat.net/topic/5348191 )
* First time using IDA Free! ( https://forum.lowyat.net/topic/5369013 )
* Using IDA Free - Part 2 ( https://forum.lowyat.net/topic/5375495 )
* Using IDA Free, Part 3, Investigate Windows syscall ( https://forum.lowyat.net/topic/5385943 )
* Introducing ProcMon, "Hack" software process ( https://forum.lowyat.net/index.php?showtopic=5001505 )
(Tullamarine, FlierMate4 and FlierMate were my forum user accounts.)
Today, I will try using PE-bear for the first time, for a simple task, finding the AddressOfEntryPoint in PE (Portable Executable) files.
PE-bear ( https://github.com/hasherezade/pe-bear ) is a tool made by malware analyst hasherezade.
Let's start! I will try analyze Windows WordPad (write.exe).
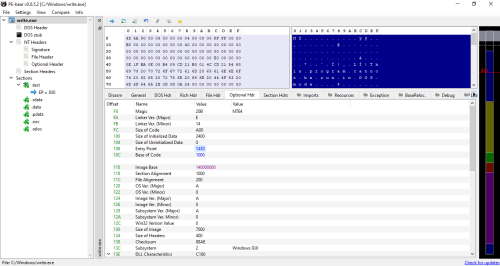
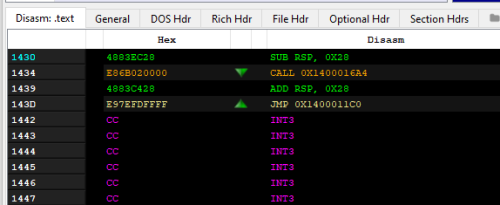
AddressOfEntryPoint is 0x1430, a Virtual Address relative to Image Base. It is runtime address in memory, not disk offset (0x830).
PE-bear disassembles the first instruction as: sub rsp, 0x20 (stack alignment commonly seen in PE32+)
I can verify the findings in PE-bear using other tools like PE Dump, or PeBytesF.exe by 440bx ( https://forum.lazarus.freepascal.org/index.php?topic=46617.0 ).
As seen in the screenshot below, AddressOfEntryPoint RVA is 0x1430, and FO (File Offset) is 0x830.
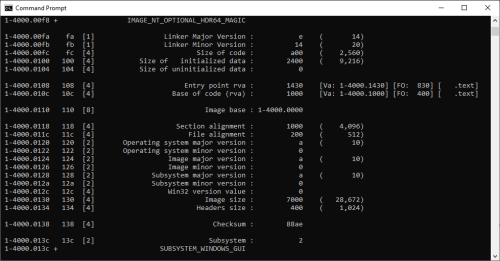
Or I can also use CFF Explorer ( https://ntcore.com/?page_id=388 ).
The last resort is using hex editor / viewer to locate the offset in Optional Header. As seen from binary analysis of PE-bear for write.exe, the offset is 0x108 from the beginning of file, but this is tricky if the PE file has custom size of DOS Stub (where I will need to read offset in 0x3C).
I think that's all for my first guide. Thank you for reading!


 Sep 4 2023, 12:50 PM, updated 3y ago
Sep 4 2023, 12:50 PM, updated 3y ago
 Quote
Quote 0.0109sec
0.0109sec
 1.07
1.07
 5 queries
5 queries
 GZIP Disabled
GZIP Disabled