It is hijacked.
CODE
dig @9.9.9.9 googie-anaiytics.com
; <<>> DiG 9.18.28 <<>> @9.9.9.9 googie-anaiytics.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 736
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;googie-anaiytics.com. IN A
;; ANSWER SECTION:
googie-anaiytics.com. 600 IN A 15.197.148.33
googie-anaiytics.com. 600 IN A 3.33.130.190
;; Query time: 405 msec
;; SERVER: 9.9.9.9#53(9.9.9.9) (UDP)
;; WHEN: Tue Aug 13 23:39:48 +08 2024
;; MSG SIZE rcvd: 81
Using the TXT query test method:
CODE
$ dig +short txt proto.on.quad9.net @9.9.9.9
(no output)
$dig +short txt proto.on.quad9.net @9.9.9.9 +tcp
do53-tcp.
$ dig +short txt proto.on.quad9.net @9.9.9.9 +tls
dot.
$ dig +short txt proto.on.quad9.net @9.9.9.9 +https=/dns-query
doh.
$ dig +short ch txt id.server. @9.9.9.9
(no output)
$ dig +short ch txt id.server. @9.9.9.9 +tcp
"res100.kul.rrdns.pch.net"
$ dig +short ch txt id.server. @9.9.9.9 +tls
"res100.kul.rrdns.pch.net"
$ dig +short ch txt id.server. @9.9.9.9 +https=/dns-query
"res100.kul.rrdns.pch.net"
Using traceroute, you can see !X (communication administratively prohibited)
CODE
$ traceroute 9.9.9.9
traceroute to 9.9.9.9 (9.9.9.9), 30 hops max, 60 byte packets
1 _gateway (192.168.137.30) 1.218 ms 1.478 ms 1.730 ms
2 * * *
3 10.223.95.65 (10.223.95.65) 72.996 ms 72.976 ms 72.966 ms
4 10.223.39.171 (10.223.39.171) 60.468 ms 10.223.39.163 (10.223.39.163) 60.453 ms 60.436 ms
5 203.82.65.113 (203.82.65.113) 72.887 ms 72.879 ms 72.944 ms
6 203.82.83.217 (203.82.83.217) 89.017 ms 203.82.83.219 (203.82.83.219) 66.107 ms 162.729 ms
7 203.82.83.34 (203.82.83.34) 199.869 ms 193.638 ms 203.82.83.32 (203.82.83.32) 199.943 ms
8 pch.myix.my (218.100.44.20) 193.591 ms 193.449 ms 193.421 ms
9 dns9.quad9.net (9.9.9.9) 193.383 ms !X 193.319 ms !X 193.282 ms !X
Let's see where they start redirecting UDP 53. Looks like the very first hop:
CODE
# traceroute -U -p53 9.9.9.9
traceroute to 9.9.9.9 (9.9.9.9), 30 hops max, 60 byte packets
1 _gateway (192.168.137.30) 2.118 ms 2.572 ms 2.818 ms
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *
11 * dns9.quad9.net (9.9.9.9) 72.977 ms *
# traceroute -T -p53 9.9.9.9
traceroute to 9.9.9.9 (9.9.9.9), 30 hops max, 60 byte packets
1 _gateway (192.168.137.30) 4.822 ms 5.259 ms *
2 * * *
3 * * *
4 * * *
5 * * *
6 * 203.82.83.219 (203.82.83.219) 54.024 ms 203.82.83.217 (203.82.83.217) 39.621 ms
7 203.82.83.34 (203.82.83.34) 59.608 ms 203.82.83.32 (203.82.83.32) 59.631 ms 59.565 ms
8 pch.myix.my (218.100.44.20) 59.553 ms 59.537 ms 59.524 ms
9 dns9.quad9.net (9.9.9.9) 65.218 ms 65.206 ms 65.193 ms
# traceroute -T -p443 9.9.9.9
traceroute to 9.9.9.9 (9.9.9.9), 30 hops max, 60 byte packets
1 _gateway (192.168.137.30) 1.799 ms 1.763 ms *
2 * * *
3 * * *
4 * * *
5 * * *
6 * dns9.quad9.net (9.9.9.9) 65.581 ms 65.325 ms
TCP port 53 and TCP port 443 have vastly different hop count. This needs further investigation.
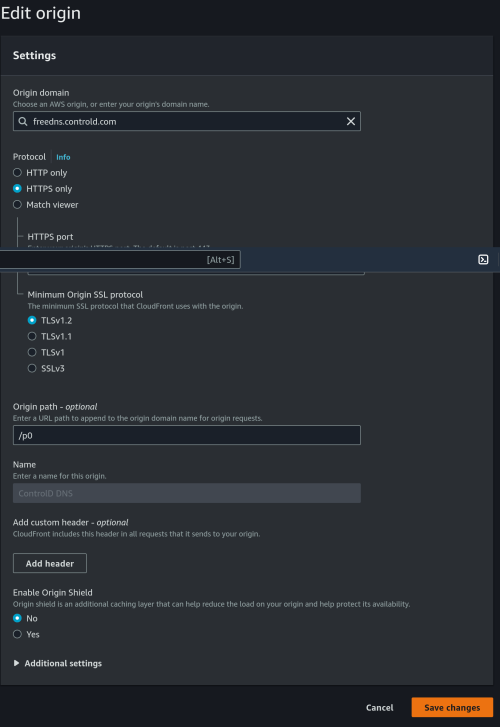
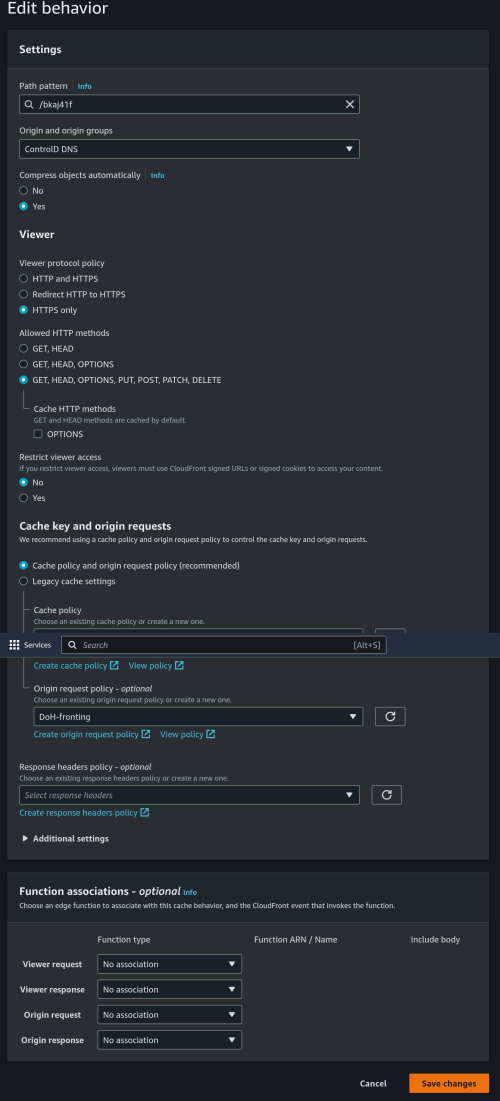
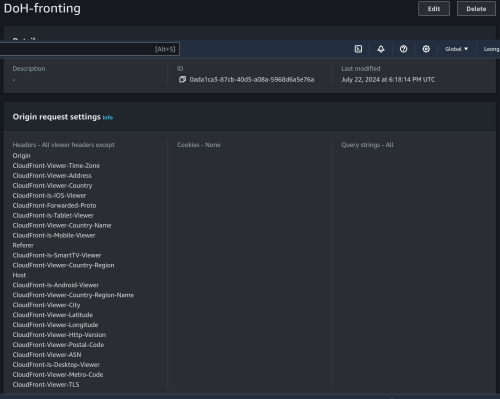
I have done a packet capture. Looks like it is man-on-the-side attack?


 Aug 14 2024, 11:52 PM
Aug 14 2024, 11:52 PM
 Quote
Quote
 0.0192sec
0.0192sec
 0.61
0.61
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled