Sep 07, 2023
3 min read
Source: https://blog.google/threat-analysis-group/a...ty-researchers/
QUOTE
Similar to the previous campaign TAG reported on, North Korean threat actors used social media sites like X (formerly Twitter) to build rapport with their targets. In one case, they carried on a months-long conversation, attempting to collaborate with a security researcher on topics of mutual interest. After initial contact via X, they moved to an encrypted messaging app such as Signal, WhatsApp or Wire. Once a relationship was developed with a targeted researcher, the threat actors sent a malicious file that contained at least one 0-day in a popular software package.
Upon successful exploitation, the shellcode conducts a series of anti-virtual machine checks and then sends the collected information, along with a screenshot, back to an attacker-controlled command and control domain. The shellcode used in this exploit is constructed in a similar manner to shellcode observed in previous North Korean exploits.
Upon successful exploitation, the shellcode conducts a series of anti-virtual machine checks and then sends the collected information, along with a screenshot, back to an attacker-controlled command and control domain. The shellcode used in this exploit is constructed in a similar manner to shellcode observed in previous North Korean exploits.
QUOTE
While our analysis of this campaign continues, we are providing an early notification of our initial findings to warn the security research community. We hope this post will remind security researchers that they could be targets of government backed attackers and to stay vigilant of security practices.
DO NOT Download the following software:
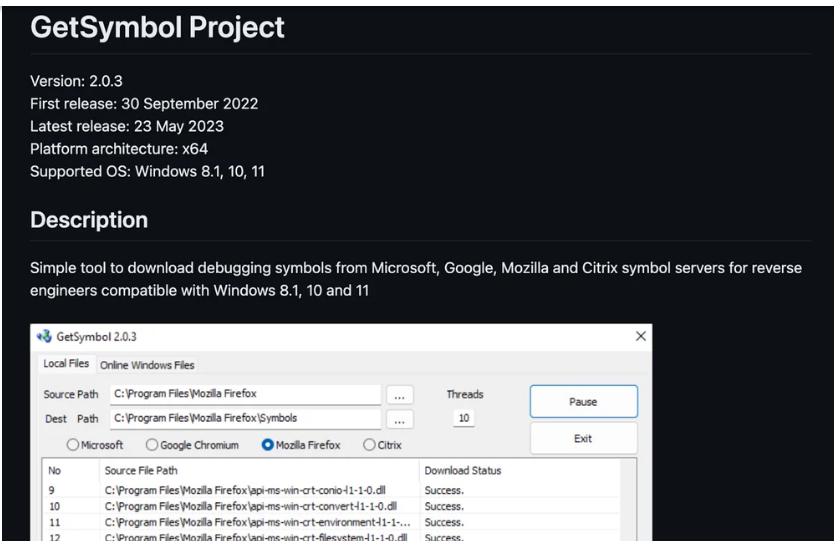
Stay Away from @paul091_ social media account.
QUOTE
Actor controlled sites and accounts
GetSymbol:
https://github[.]com/dbgsymbol/
https://dbgsymbol[.]com
50869d2a713acf406e160d6cde3b442fafe7cfe1221f936f3f28c4b9650a66e9
0eedfd4ab367cc0b6ab804184c315cc9ce2df5062cb2158338818f5fa8c0108e
2ee435bdafacfd7c5a9ea7e5f95be9796c4d9f18643ae04dca4510448214c03c
5977442321a693717950365446880058cc2585485ea582daa515719c1c21c5bd
C2 IPs/Domains:
23.106.215[.]105
www.blgbeach[.]com
X (formerly Twitter) Accounts
https://twitter.com/Paul091_
Wire Accounts
@paul354
Mastodon Account:
https://infosec.exchange/@paul091_
GetSymbol:
https://github[.]com/dbgsymbol/
https://dbgsymbol[.]com
50869d2a713acf406e160d6cde3b442fafe7cfe1221f936f3f28c4b9650a66e9
0eedfd4ab367cc0b6ab804184c315cc9ce2df5062cb2158338818f5fa8c0108e
2ee435bdafacfd7c5a9ea7e5f95be9796c4d9f18643ae04dca4510448214c03c
5977442321a693717950365446880058cc2585485ea582daa515719c1c21c5bd
C2 IPs/Domains:
23.106.215[.]105
www.blgbeach[.]com
X (formerly Twitter) Accounts
https://twitter.com/Paul091_
Wire Accounts
@paul354
Mastodon Account:
https://infosec.exchange/@paul091_
This post has been edited by MatQuasar: Sep 8 2023, 02:58 PM


 Sep 8 2023, 02:56 PM, updated 3y ago
Sep 8 2023, 02:56 PM, updated 3y ago
 Quote
Quote
 0.0149sec
0.0149sec
 0.54
0.54
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled