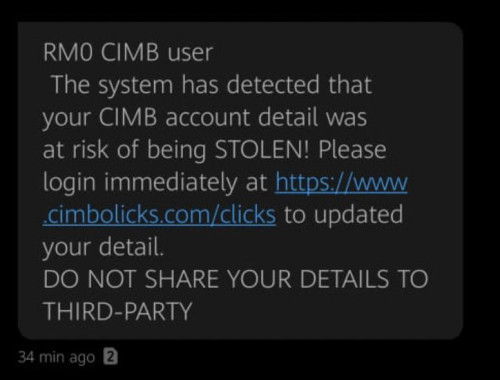
the fishing link is
CODE
https://www dot cimb o licks dotcom/clicks/
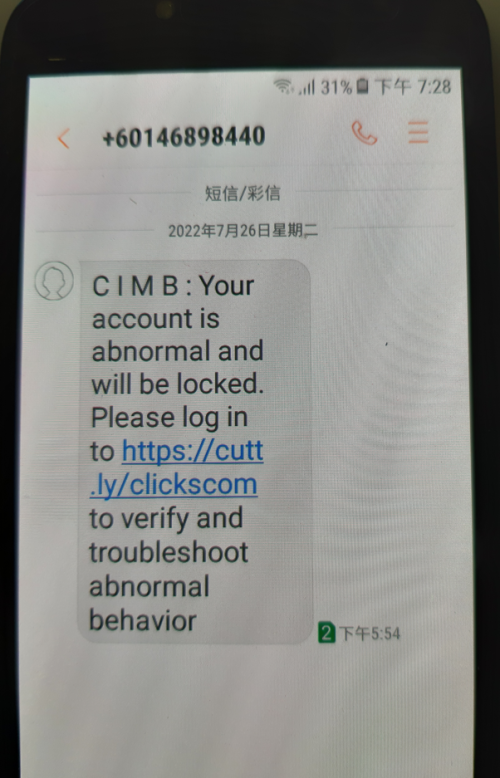
http://103 dot 97.3 dot 130/clicks
see some of their php code snippet here:
CODE
hostname + /clicks/api/login/submit_username?username=suckerzzz&deviceId=lameaf
some facts?
- domain name went live ~ 2 weeks ago.
- attacker hosted from china/hongkong guangzhou region.
- coder probably cina mainlanders, judging from the cinis comment on their php code
- it may have geoblock too far countries like USA? this theory is not verified yet.
- the php first check for smartphone useragent, if you use browser, it will redirect to legit banking website without even loading a single byte of the spoof code (change ur useragent in devtools>more tools>network condition)
- attacker use websocket to sent back response to client after victim submit the username.
(reason behind this is i think is so attacker can relay the legit secureWord back to their fising site, high possibility that they manually validate the username. also it means got person manning behind the computer to do those validating stuff after they launch their fishing campaign via sms/whatsapp)
- i have no gone pass the enter password part because no response from the websocket after i submit the id. lol.
CODE
Domain Name: cimb o licks dot com
Registry Domain ID: 2710744632_DOMAIN_COM-VRSN
Registrar WHOIS Server: grs-whois.hichina.com
Registrar URL: http://wanwang.aliyun.com
Updated Date: 2022-07-13T17:06:01Z
Creation Date: 2022-07-13T17:06:00Z
Registrar Registration Expiration Date: 2023-07-13T17:06:00Z
Registrar: Alibaba Cloud Computing Ltd. d/b/a HiChina (www.net.cn)
Registrar IANA ID: 1599
Reseller:
Domain Status: clientHold https://icann.org/epp#clientHold
Domain Status: serverHold https://icann.org/epp#serverHold
Registrant City:
Registrant State/Province:
Registrant Country:
Registrant Email:https://whois.aliyun.com/whois/whoisForm
Registry Registrant ID: Not Available From Registry
Name Server: DNS25.HICHINA.COM
Name Server: DNS26.HICHINA.COM
DNSSEC: unsigned
Registrar Abuse Contact Email: email@service.aliyun.com
Registrar Abuse Contact Phone: +86.95187
thx
This post has been edited by taga: Jul 25 2022, 04:42 AM


 Jul 25 2022, 04:37 AM, updated 4y ago
Jul 25 2022, 04:37 AM, updated 4y ago
 Quote
Quote
 0.0209sec
0.0209sec
 0.92
0.92
 5 queries
5 queries
 GZIP Disabled
GZIP Disabled