QUOTE(FlierMate1 @ Jun 18 2022, 04:56 AM)
Here comes the third year of small file competition organized by a group of security researcher or reverse engineer:
tmpout.sh/bggp/3/
Unlike the prior contests in 2020 and 2021, this year's contest will involve a lot of creative thinking.
Now I will become more like ethical hacker...
I don't dare to try the last two scenario. If I were able to create EXE that crashes Windows, I will be in the tech news headline tomorrow. Smile
This contest runs from June 17th 2022 to August 19th 2022 (New York time)
@angch, I see you followed @binarygolf on Twitter. Nice to see you there! This year contest is more challenging, isn't it?
Meh. It's just a fuzzing challenge. Boring.tmpout.sh/bggp/3/
Unlike the prior contests in 2020 and 2021, this year's contest will involve a lot of creative thinking.
Now I will become more like ethical hacker...
I don't dare to try the last two scenario. If I were able to create EXE that crashes Windows, I will be in the tech news headline tomorrow. Smile
This contest runs from June 17th 2022 to August 19th 2022 (New York time)
@angch, I see you followed @binarygolf on Twitter. Nice to see you there! This year contest is more challenging, isn't it?
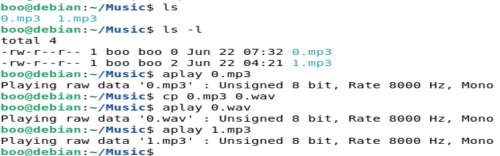
Start here: Divide by zero.
Edit: Wait. Re-reading instructions.
This post has been edited by angch: Jun 18 2022, 01:39 PM


 Jun 18 2022, 01:34 PM
Jun 18 2022, 01:34 PM

 Quote
Quote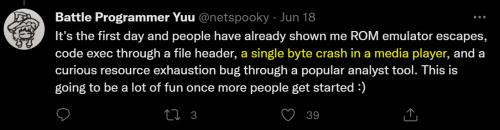
 0.0166sec
0.0166sec
 0.78
0.78
 6 queries
6 queries
 GZIP Disabled
GZIP Disabled