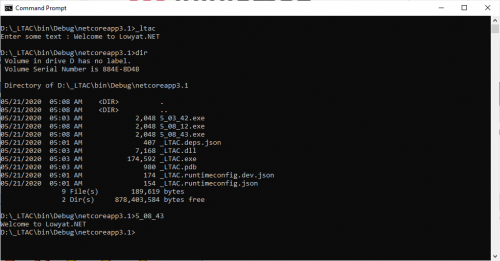
To get me started, I build this console app (Release, Any CPU) on my Windows 10 using .NET Framework 4.7.1.
CODE
using System;
namespace HelloWorld
{
class Program
{
static void Main(string[] args)
{
Console.WriteLine("Hello World");
}
}
}
namespace HelloWorld
{
class Program
{
static void Main(string[] args)
{
Console.WriteLine("Hello World");
}
}
}
After that, I run a CLI tool to dump the PE of HelloWorld.exe (4608 bytes):
CODE
[DOS Header]
NT Headers RVA : 0x00000080
[File Header]
Machine : 0x014C
IMAGE_FILE_MACHINE_I386 0x0000014C
Number Of Section : 3
Linked At : 0xB2A5CFAC (2064-12-23 06:37:32)
Optional Header Size : 224
Characteristics : 0x00000022
IMAGE_FILE_EXECUTABLE_IMAGE 0x00000002
IMAGE_FILE_LARGE_ADDRESS_AWARE 0x00000020
[Optional Header]
Magic : 0x10B
IMAGE_NT_OPTIONAL_HDR32_MAGIC 0x0000010B
ImageBase : 0x00400000
Base Of Code : 0x00002000
Base Of Data : 0x00004000
OEP : 0x00002702
Section Alignment : 0x2000
File Alignment : 0x200
Linker Version : 48.0
OS Version : 4.0
Image Version : 0.0
Subsystem Version : 6.0
Image Size : 0x8000
Code Size : 0x800
Headers Size : 0x200
CheckSum : 0x00000000
Subsystem : 3
IMAGE_SUBSYSTEM_WINDOWS_CUI 0x00000003
Dll Characteristics : 0x00008560
Data Directory Size : 16
Loader Flags : 0x00000000
[Data Directory]
Name RVA Size
Export Table (N/A) (N/A)
Import Table 0x000026AD 0x0000004F
Resource Table 0x00004000 0x000005BC
Exception Table (N/A) (N/A)
Security Table (N/A) (N/A)
Base relocation Table 0x00006000 0x0000000C
Debug 0x00002634 0x00000038
Copyright (N/A) (N/A)
Global Pointer (N/A) (N/A)
Thread local storage (N/A) (N/A)
Load Configuration (N/A) (N/A)
Bound Import Table (N/A) (N/A)
Import Address Table 0x00002000 0x00000008
Delay Import Descriptor (N/A) (N/A)
COM Header 0x00002008 0x00000048
Reserved (N/A) (N/A)
[Sections]
Name RVA V.Size RAW R.Size Characteristics
.text 0x00002000 0x00000708 0x00000200 0x00000800 0x60000020
.rsrc 0x00004000 0x000005BC 0x00000A00 0x00000600 0x40000040
.reloc 0x00006000 0x0000000C 0x00001000 0x00000200 0x42000040
[Import Table]
mscoree.dll
0 _CorExeMain
NT Headers RVA : 0x00000080
[File Header]
Machine : 0x014C
IMAGE_FILE_MACHINE_I386 0x0000014C
Number Of Section : 3
Linked At : 0xB2A5CFAC (2064-12-23 06:37:32)
Optional Header Size : 224
Characteristics : 0x00000022
IMAGE_FILE_EXECUTABLE_IMAGE 0x00000002
IMAGE_FILE_LARGE_ADDRESS_AWARE 0x00000020
[Optional Header]
Magic : 0x10B
IMAGE_NT_OPTIONAL_HDR32_MAGIC 0x0000010B
ImageBase : 0x00400000
Base Of Code : 0x00002000
Base Of Data : 0x00004000
OEP : 0x00002702
Section Alignment : 0x2000
File Alignment : 0x200
Linker Version : 48.0
OS Version : 4.0
Image Version : 0.0
Subsystem Version : 6.0
Image Size : 0x8000
Code Size : 0x800
Headers Size : 0x200
CheckSum : 0x00000000
Subsystem : 3
IMAGE_SUBSYSTEM_WINDOWS_CUI 0x00000003
Dll Characteristics : 0x00008560
Data Directory Size : 16
Loader Flags : 0x00000000
[Data Directory]
Name RVA Size
Export Table (N/A) (N/A)
Import Table 0x000026AD 0x0000004F
Resource Table 0x00004000 0x000005BC
Exception Table (N/A) (N/A)
Security Table (N/A) (N/A)
Base relocation Table 0x00006000 0x0000000C
Debug 0x00002634 0x00000038
Copyright (N/A) (N/A)
Global Pointer (N/A) (N/A)
Thread local storage (N/A) (N/A)
Load Configuration (N/A) (N/A)
Bound Import Table (N/A) (N/A)
Import Address Table 0x00002000 0x00000008
Delay Import Descriptor (N/A) (N/A)
COM Header 0x00002008 0x00000048
Reserved (N/A) (N/A)
[Sections]
Name RVA V.Size RAW R.Size Characteristics
.text 0x00002000 0x00000708 0x00000200 0x00000800 0x60000020
.rsrc 0x00004000 0x000005BC 0x00000A00 0x00000600 0x40000040
.reloc 0x00006000 0x0000000C 0x00001000 0x00000200 0x42000040
[Import Table]
mscoree.dll
0 _CorExeMain
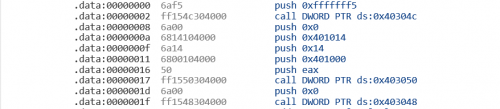
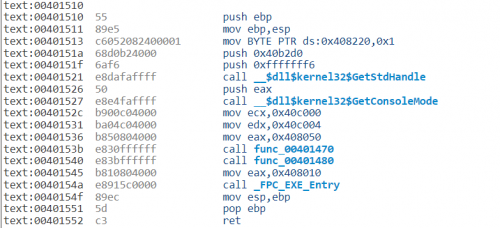
If I understand correctly, the code section starts at 0x00402000 given the below:
ImageBase : 0x00400000
Base Of Code : 0x00002000
I am not sure if I am using the proper disassembler, because I just choose one randomly: https://onlinedisassembler.com/
I cannot seem to find the x86 instruction that make CALL DWORD PTR [XXXXXXXX] from 0x00402000 to 0x00402708. There must be a call made to the Win32 API, or mscoree.dll specifically?
While I have some good progress since my last attempt to understand Windows PE (especially "PE Dump" comes handy), I still have a long way to go to construct my own Windows PE in the simplest form.
My initial plan is to support compilation of following commands:
(1) Console.WriteLine
(2) Console.Write
(3) Console.ReadLine
Any help is greatly appreciated.
Reference: https://docs.microsoft.com/en-us/archive/ms...ormat-in-detail
* Mussel and Tullamarine are the same middle-aged guy


 Apr 10 2020, 03:04 PM, updated 6y ago
Apr 10 2020, 03:04 PM, updated 6y ago
 Quote
Quote
 0.0250sec
0.0250sec
 0.40
0.40
 5 queries
5 queries
 GZIP Disabled
GZIP Disabled